Why is it Important for Cybersecurity Firms to Understand SEO?
In today’s digital landscape, cybersecurity firms face unprecedented competition for client attention, with search engine visibility often determining which providers secure valuable contracts. Search Engine Optimization (SEO), operating at the intersection of marketing strategy and technical implementation, enables security-focused businesses to position themselves effectively before decision-makers at critical moments. While many security professionals excel at protecting digital assets, they frequently overlook the algorithmic frameworks that determine online discoverability, potentially surrendering market position to competitors with inferior solutions but superior search presence. Understanding SEO is critical to ranking on search engines and connecting with your potential customers.
Key Takeaways
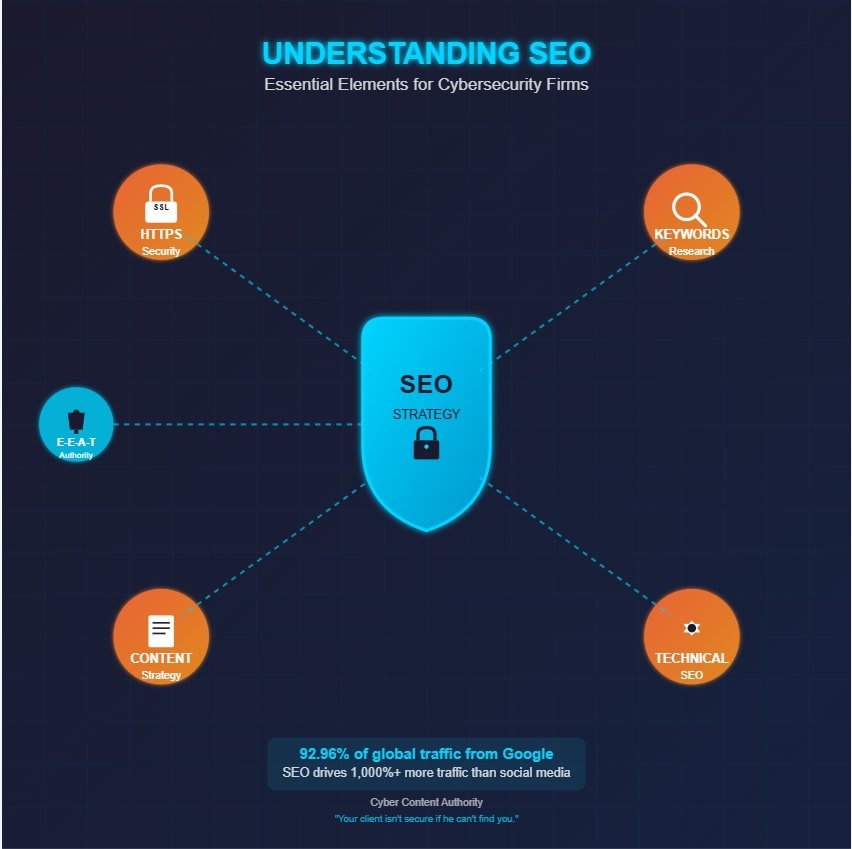
- HTTPS certification and security-focused schema markup serve as ranking factors and build credibility with potential clients.
- Focus on keyword research targeting decision-makers with technical terms and emerging threat terminology like “AI-powered phishing.”
- Create content mapped to the buyer’s journey: awareness, consideration, and decision stages for maximum relevance.
- Implement proper technical SEO foundations to avoid common pitfalls like slow page speeds and JavaScript rendering issues.
- Establish expertise through E-E-A-T signals and authoritative backlinks from recognized industry sources to build long-term authority.
Why Understanding SEO Matters for Cybersecurity Companies

In today’s digital landscape, understanding SEO by learning about the five critical factors that elevate search engine optimization from a mere marketing tactic to an essential business strategy for cybersecurity firms operating in an increasingly competitive marketplace.
Enhanced visibility allows security providers to distinguish themselves, while established credibility, through content strategies focusing on thought leadership, becomes paramount in an industry where trust determines purchase decisions. Moreover, 92.96% of global traffic comes from Google Search, Images, and Maps, making it crucial for cybersecurity firms to prioritize SEO.
Additionally, sophisticated audience targeting connects solutions with businesses actively seeking protection, thereby transforming visitors into qualified leads through optimized conversion pathways. The compounding nature of SEO investments yields sustained market positioning and long-term ROI, which, unlike paid advertising, continues delivering value after implementation. SEO also provides cost-effective marketing solutions compared to traditional advertising channels, maximizing return on marketing investments for cybersecurity businesses.
The Three Stages of the Buyer’s Journey in Cybersecurity
When traversing the complex landscape of cybersecurity purchasing decisions, organizations progress through three distinct stages, each characterized by unique informational needs, evaluation criteria, and decision-making processes.
Throughout the awareness stage, highly technical buyer personas seek trend-focused content through industry publications. During consideration, these stakeholders engage in comparative analysis across multiple vendors. Finally, at the decision stage, case studies and technical specifications become paramount. Additionally, 75.7% of marketers use AI tools on a regular basis to enhance content relevance and effectiveness.
Consequently, effective content mapping requires meticulous alignment with each journey phase, whereby organizations strategically deploy data-driven narratives, incorporating relevant statistics and trend updates, thereby establishing credibility throughout the extended sales cycle. Creating effective content that resonates with target audiences helps build trust and influences purchasing decisions, particularly critical in the highly sensitive cybersecurity market.
Essential Technical SEO Elements for Security Websites
For cybersecurity firms, implementing security-focused schema markup represents a critical technical SEO component. This structured data helps search engines understand the specific security services offered while enhancing rich snippet opportunities in search results. Additionally, SEO drives 1,000%+ more traffic than organic social media, making it an essential focus for firms aiming to increase their online visibility. Not understanding SEO in this regard can be why your pages aren’t appearing on search engines.
The HTTPS certification process, which involves obtaining and properly installing SSL certificates through a trusted Certificate Authority (CA), serves as both a ranking factor and trust signal. It demonstrates the firm’s commitment to secure communications. Websites with HTTPS security receive a direct ranking boost from Google, providing an immediate competitive advantage in search results.
Beyond mere compliance with search engine preferences, these technical implementations establish credibility within the industry. This is particularly important for organizations that must project security expertise through every aspect of their digital presence, including their website’s technical foundation.
Security Schema Implementation
Structured data implementation represents one of the most vital, yet frequently overlooked, components of technical SEO strategy for cybersecurity firms seeking to establish digital authority.
Through strategic deployment of specialized schema types, including Organization and Product/Service markup, security companies can notably enhance their SERP visibility while providing search engines with essential contextual information about their expertise and offerings.
Implementation tools, such as Google’s Structured Data Testing Tool, facilitate proper validation of JSON-LD markup—Google’s preferred format due to its flexibility and security advantages—ensuring cybersecurity websites meet technical requirements while avoiding penalties for incorrect schema application.
This remains particularly important in an industry where credibility and trust are paramount. Implementing the right schema markup types allows cybersecurity websites to be displayed more prominently in search results through rich snippets, potentially increasing click-through rates and conversions.
HTTPS Certification Process
A robust HTTPS certification process constitutes the bedrock of technical SEO implementation for cybersecurity firms, serving not merely as a security protocol but as an essential trust signal that considerably impacts search visibility and user confidence.
The certification mechanism, orchestrated through trusted Certificate Authorities (CAs), implements Multi-Perspective Issuance Corroboration (MPIC) among advanced certificate validation methods to prevent BGP attacks and enhance domain control validation from multiple geographic perspectives. Automated certificate linting helps ensure that X.509 certificates are properly formatted and compliant with industry standards.
When properly configured, these encryption techniques—utilizing X.509 certificate formats with appropriate key lengths—protect against man-in-the-middle attacks while simultaneously satisfying search engines’ preference for secure connections, thereby improving SERP rankings while meeting regulatory compliance requirements across jurisdictions.
Keyword Research Strategies for Security Solutions
Effective keyword research for cybersecurity firms requires a strategic approach that precisely targets the decision-makers who influence security purchases within organizations, typically C-suite executives and IT directors with specific technical concerns and regulatory compliance needs. Additionally, understanding that Google uses over 200 factors in their ranking algorithm can help firms optimize their keyword strategy effectively.
By conducting thorough analyses of competitor terminology and search patterns, security firms can identify valuable semantic gaps in the marketplace, where potential clients may be searching for solutions that competing providers have inadequately addressed or overlooked entirely. The implementation of long-tail technical keywords, such as “zero-day vulnerability protection for financial institutions” or “GDPR-compliant cloud security monitoring solutions,” enables cybersecurity providers to capture highly qualified traffic with demonstrably greater conversion potential, as these searches typically indicate advanced stages in the security solution procurement process. Incorporating emerging threat terminology like “AI-powered phishing” ensures content remains relevant to organizations seeking protection against evolving cyber threats.
Targeting Security Decision-Makers
Successful keyword research strategies for cybersecurity firms must precisely align with the complex decision-making frameworks employed by security professionals, CISOs, and IT executives who evaluate and procure enterprise protection solutions.
Effective targeting requires understanding both technical requirements and business priorities that influence user trust in security vendors, particularly when high-value investments are contemplated.
When developing keyword clusters, organizations should categorize terms according to decision-making stages, incorporating both technical specifications required by implementation teams and ROI-focused language that resonates with executives.
Mapping keywords to the appropriate stage of the buyer journey helps create more relevant content that addresses specific customer needs at each decision point.
Additionally, content should address specific pain points within vertical industries, thereby demonstrating domain expertise while simultaneously capturing long-tail search traffic from security professionals seeking industry-specific solutions.
Competitor Term Analysis
Three critical dimensions of competitor term analysis provide cybersecurity firms with strategic intelligence necessary for outmaneuvering rivals in increasingly contested digital marketplaces, particularly as security solution providers struggle to differentiate their offerings amid growing market saturation.
Through thorough competitor analysis, security firms can identify high-performing keywords driving traffic to competitive websites, while simultaneously evaluating content quality surrounding these terms. Effective competitive analysis enhances sustained success by enabling firms to craft unique value propositions that resonate with target audiences.
In addition, by examining competitors’ backlink profiles, organizations can uncover strategic link-building opportunities that enhance domain authority.
Finally, traffic pattern analysis across competitor domains reveals seasonal fluctuations and engagement metrics that, when properly interpreted, illuminate potential market gaps where innovative cybersecurity messaging can effectively penetrate decision-maker consciousness.
Long-Tail Technical Keywords
Long-tail technical keywords represent an advanced targeting approach for cybersecurity firms seeking to distinguish themselves beyond primary competitive landscapes, particularly as attention shifts from broader competitor strategies to precise audience engagement mechanisms.
These specialized keyword phrases, typically containing three or more words, deliver substantial long tail benefits through their specificity and alignment with high-intent search queries, thereby enhancing conversion potential for security-focused businesses. Utilizing these keywords enables cybersecurity startups to compete against established competitors by focusing on niche segments where larger companies may not have specialized content.
- Strategic placement within page titles, meta descriptions, and content headings maximizes keyword impact while maintaining natural content flow.
- Implementation of industry-specific technical terminology attracts qualified prospects with demonstrated purchase intent.
- Geographic modifiers create localized relevance for regional cybersecurity service providers.
- Regular performance analysis enables continuous optimization of keyword selection based on measurable conversion metrics.
Creating Content That Converts Security-Conscious Clients

While developing a robust SEO strategy provides the foundation for cybersecurity marketing success, creating compelling content that specifically addresses the concerns of security-conscious clients represents the critical bridge between visibility and conversion.
Effective content personalization, which leverages AI and machine learning capabilities, enables cybersecurity firms to craft messaging that resonates with specific audience segments based on their unique threat landscapes and compliance requirements. Additionally, link-building strategies such as digital PR and guest posting can enhance content reach and credibility.
Through security storytelling that emphasizes transparency, measurable results, and regulatory adherence, organizations can build the trust necessary to convert prospects who, according to research, will actively avoid brands they perceive as inadequately protecting data—a concern held by 70% of consumers. Focusing on topics like GRC, identity, and cloud security has proven especially effective in engaging cybersecurity professionals seeking practical solutions to their challenges.
On-Page Optimization Techniques for Cybersecurity Topics
Effective on-page optimization for cybersecurity topics demands a sophisticated approach that balances technical precision with conversion-focused content strategy, particularly as search engines increasingly prioritize expertise, authoritativeness, and trustworthiness in this sensitive field.
Optimizing cybersecurity content requires balancing technical precision with conversion strategy while demonstrating trustworthiness in this sensitive domain.
In addition, content optimization requires meticulous keyword placement within properly structured documents that utilize schema markup to enhance visibility. Creating content that addresses common security inquiries can significantly improve your website’s relevance and user engagement.
- Implement thorough keyword research to identify high-value cybersecurity terminology that aligns with both search intent and business objectives
- Structure content hierarchically using H1-H3 tags that incorporate primary and secondary keywords
- Deploy schema markup to provide search engines with explicit context about technical security content
- Establish robust internal linking architectures that connect pillar pages to supporting cluster content
Measuring Your SEO Success: Key Performance Indicators
Successful measurement of SEO effectiveness for cybersecurity firms requires a sophisticated analytics framework that captures both technical performance metrics and business impact indicators, ultimately providing actionable intelligence for continuous optimization.
When establishing SEO Benchmarks, organizations should prioritize organic traffic volume, keyword rankings, and conversion rates, which collectively illuminate the efficacy of current strategy implementations.
Comprehensive Metric Analysis must incorporate cybersecurity-specific considerations, including domain authority, backlink quality, and secure protocol implementation (HTTPS), while simultaneously accounting for user engagement metrics such as bounce rate and average session duration—all of which contribute to search engine trust and visibility within increasingly competitive cybersecurity market segments. Effective SEO strategies should also include regular security incident detection metrics to demonstrate your firm’s expertise and capabilities to potential clients.
Common SEO Pitfalls in the Cybersecurity Industry

Moving beyond performance measurement, cybersecurity firms must navigate a treacherous landscape of SEO challenges that can undermine even the most robust digital marketing efforts.
Within this complex digital ecosystem, where technical expertise intersects with content creation, organizations frequently stumble into predictable pitfalls that hinder user engagement and dilute their online authority.
- Technical SEO Deficiencies – JavaScript rendering issues and slow page speeds, which are particularly relevant for security-focused websites with complex infrastructures.
- Content Misalignment – Over-reliance on technical jargon without proper content diversification. Many firms fail to communicate solutions effectively, leading to 90% of breaches resulting from human error when technical concepts aren’t properly understood.
- Flawed Link-Building Strategies – Prioritizing quantity over quality, resulting in diminished domain authority.
- Inadequate Strategic Planning – Insufficient keyword research that fails to capture evolving threat landscapes.
Building a Sustainable SEO Strategy for Long-Term Growth
While short-term tactical maneuvers may yield temporary visibility spikes, cybersecurity firms seeking enduring digital relevance must architect thorough SEO frameworks that withstand algorithm fluctuations, competitive pressures, and evolving threat landscapes.
Sustainable strategies require demonstrating expertise through extensive E-E-A-T signals, which, when coupled with authoritative backlinks from industry-recognized sources, establish credibility within the cybersecurity ecosystem.
Additionally, continuous refinement of technical foundations—including site speed optimization, mobile responsiveness, and enhanced security protocols—ensures long-term benefits that extend beyond mere visibility, ultimately contributing to pipeline growth and increased annual recurring revenue through organic search performance. Companies should consider partnering with agencies that provide technical SEO audits as part of their comprehensive service offerings to maintain competitive advantage.
Understanding SEO Can Make Your Business Grow through Better and More Client Connections
Implementing a thorough SEO strategy represents an essential investment for cybersecurity firms seeking to enhance visibility in an increasingly competitive digital landscape. Through meticulous keyword research, technical optimization, and strategically aligned content development that addresses the specific concerns of security-conscious decision-makers throughout their buyer’s journey, organizations can effectively establish authority, generate qualified leads, and ultimately secure long-term growth within the specialized cybersecurity marketplace.
Frequently Asked Questions
How Long Does It Take to See Results From SEO Efforts?
SEO results typically emerge within 3-6 months, with significant keyword research impacts visible after 6-12 months of consistent effort. Measurable organic traffic improvements depend on implementation sophistication and competitive landscape dynamics.
Should Cybersecurity Firms Prioritize Local or Global SEO Strategies?
Cybersecurity firms should choose based on target markets. Local refinement delivers focused results for regional clients, while global reach strategies open international opportunities. The ideal approach combines both for maximal competitive advantage.
How Do Algorithm Updates Affect Cybersecurity SEO Strategies?
Algorithm updates greatly impact cybersecurity SEO strategies, requiring firms to adapt content quality and technical specifications to maintain search ranking. Innovative approaches focusing on expertise and trustworthiness become essential amid evolving algorithmic priorities.
Can SEO Help During Cybersecurity Product Launches?
SEO greatly enhances cybersecurity product launches by boosting product visibility and complementing the launch strategy. It attracts targeted traffic, establishes market positioning, and creates sustainable digital presence beyond initial release momentum.
How Does SEO Differ for B2B Versus B2C Cybersecurity Companies?
B2B cybersecurity SEO focuses on technical, niche B2B keywords targeting stakeholders in extended sales cycles, while B2C content emphasizes consumer-friendly messaging with broader appeal and shorter conversion paths.


