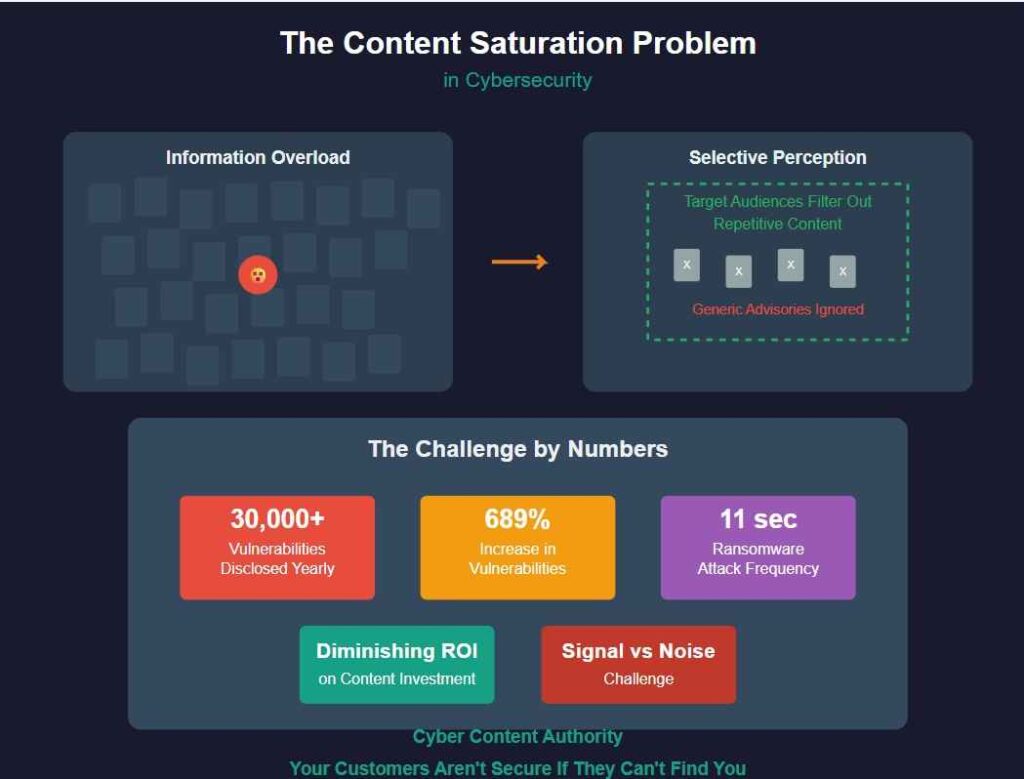
The cybersecurity content landscape faces unprecedented content saturation, with practitioners struggling to distinguish valuable insights from information overload. Organizations encounter diminishing returns on their content investments as target audiences, bombarded with repetitive security advisories and generic best practices, develop selective perception mechanisms. To effectively penetrate this cluttered environment, security professionals must implement strategic differentiation tactics that enhance signal-to-noise ratios, establish authoritative positioning, and deliver actionable intelligence. The following strategies offer an extensive framework for achieving meaningful engagement.
Key Takeaways
- Establish cybersecurity thought leadership in specialized niches rather than producing high-volume, general content.
- Utilize data visualization techniques to transform complex threat intelligence into comprehensible, actionable narratives.
- Focus on audience segmentation to deliver customized messaging that addresses specific stakeholder concerns and needs.
- Create technical deep-dives into emerging threats like quantum vulnerabilities to differentiate from surface-level content.
- Leverage strategic content distribution across multiple channels including podcasts, webinars, and social media to maximize reach.
Prioritize Quality Over Quantity in Cybersecurity Content

While organizations often rush to produce voluminous cybersecurity materials in response to emerging threats, the strategic prioritization of quality over quantity represents a fundamental paradigm shift that yields substantial dividends across operational, reputational, and compliance dimensions.
Through systematic content curation, organizations can eliminate redundant information and focus on delivering actionable, evidence-based insights that address specific threat vectors relevant to their stakeholders. Additionally, implementing keyword targeting strategies ensures that content aligns with the search intent of key audiences, further enhancing visibility and engagement.
Furthermore, effective audience segmentation guarantees that critical security communications reach appropriate recipients with customized messaging that aligns with their technical proficiency, role-specific vulnerabilities, and decision-making authority, thereby enhancing engagement, retention, and ultimately, organizational security posture. Many companies prefer implementing the qualitative assessment approach initially due to its simplicity and ability to quickly identify key risks before determining if more detailed analysis is needed.
Leverage Data-Driven Insights to Cut Through the Noise
In today’s cybersecurity landscape, where information overload threatens effective decision-making, organizations must filter their analytical approach to focus exclusively on actionable metrics that directly influence security posture and risk management.
Security professionals, when confronted with vast quantities of threat intelligence and log data, can extract meaningful patterns through advanced visualization techniques that transform complex datasets into comprehensible security trends, anomalies, and potential attack vectors. Integrating a SERP scraping API enables cybersecurity teams to access real-time security information from diverse online sources that traditional data mining might miss. Technical SEO strategies for securing compliance can also enhance the efficacy of these analytical tools.
Critical indicators, including unusual authentication attempts, privilege escalation events, and indicators of compromise that align with the organization’s specific threat profile, should receive prioritized attention through automated filtering systems, thereby enabling security teams to respond to genuine threats rather than chasing false positives.
Actionable Metrics Only
Distinguishing actionable metrics from vanity measurements represents a fundamental challenge for cybersecurity professionals seeking to implement data-driven security programs. Through metric benchmarking, organizations can identify which indicators truly drive security improvements versus those creating noise, particularly when evaluating incident severity levels against industry standards. Tracking incident response time provides critical insight into organizational readiness against evolving cyber threats.
| Actionable Metrics | Non-Actionable Vanity Metrics |
|---|---|
| Mean Time to Contain (MTTC) | Total alerts generated |
| Vulnerability Remediation Time | Number of deployed tools |
| Phishing Click Rate Post-Training | Security budget size |
| Third-Party Risk Assessment Scores | Website visits to security portal |
Effective metric selection requires ruthless prioritization, focusing exclusively on measurements that facilitate clear decision-making and resource allocation, while systematically eliminating data points that, despite their impressive appearance, fail to enhance security outcomes.
Visualize Security Patterns
Visualizing security data transforms overwhelming information streams into coherent, interpretable narratives that security teams can promptly act upon, effectively bridging the gap between raw data and strategic defense postures.
By leveraging advanced visual processing capabilities, organizations can greatly enhance pattern recognition while reducing cognitive load for analysts who must rapidly distinguish between normal operations and potential threats.
The implementation of visualization strategies yields three primary advantages:
- Accelerated anomaly detection through heat maps and timeline graphs that highlight deviations from established baselines.
- Enhanced comprehension of attack vectors via network graphs showing relationship patterns between system components.
- Improved cross-functional communication through visual representations that translate complex technical data into stakeholder-appropriate insights.
This approach is particularly critical as thousands of malware attacks are recorded daily, requiring security teams to quickly identify and prioritize emerging threats.
Prioritize Critical Indicators
How organizations identify which security signals warrant immediate attention determines whether security teams can effectively respond to threats or become paralyzed by information overload.
Effective threat prioritization requires implementing real-time monitoring systems that track key cybersecurity metrics, including MTTD, MTTR, and security incident counts, which collectively enable data-driven decision-making during critical events.
Organizations should adopt a risk-based approach to vulnerability management, wherein assets are evaluated based on business criticality rather than technical severity alone.
Integrating CTI with existing security frameworks helps security teams focus on the approximately 6% of vulnerabilities that are actually exploited in the wild, significantly reducing the noise created by low-risk findings.
Through thorough metrics assessment and continuous monitoring, security teams can strategically allocate resources to high-impact vulnerabilities, greatly reducing noise while maintaining visibility across all potential attack vectors.
Develop a Unique Content Angle in the Cybersecurity Space
Organizations seeking to distinguish their cybersecurity messaging should consider specialized approaches, such as technical deep-dives into niche vulnerabilities that explore zero-day exploits or firmware-level attacks beyond what typical industry analysis provides. Additionally, tracking engagement rates across various content formats can enhance understanding of audience preferences and improve content targeting.
Examining threat actor psychographics, including criminal motivation patterns, group dynamics, and operational methodologies across different APT groups, offers valuable context that transforms generic threat intelligence into actionable security insights. As geopolitical tensions continue to rise, organizations should discuss how 97% of companies reported increased cyber threats since the Russia-Ukraine conflict began in 2022.
Niche Technical Deep-Dives
Three critical dimensions of cybersecurity have emerged as particularly fertile ground for developing unique content angles that address sophisticated technical challenges within the rapidly evolving threat landscape.
Organizations seeking differentiation in saturated cybersecurity discourse should focus on technical deep-dives that examine complex intersections of emerging threats and defensive capabilities, particularly where AI Adaptation Techniques intersect with the Cyber Threat Lifecycle. The recent exploitation of zero-day vulnerabilities in Ivanti technology demonstrates the urgent need for specialized content addressing emerging attack vectors.
- Quantum-resistant cryptographic implementation strategies that address post-quantum vulnerabilities
- Zero-trust architecture deployment methodologies for multi-cloud environments
- AI-driven anomaly detection systems that counter sophisticated, adaptive malware
These niches represent underexplored technical territories where specialized knowledge can establish thought leadership while providing actionable intelligence for security professionals traversing increasingly complex threat matrices.
Threat Actor Psychographics
While technical deep-dives provide critical infrastructure knowledge, the psychology behind threat actors represents an equally compelling frontier for cybersecurity content differentiation.
Within this underexplored terrain, organizations can develop superior defense mechanisms by analyzing threat actor traits across multiple dimensions, including financial motivations, revenge impulses, and technological acquisition desires.
The strategic value of understanding psychological tactics emerges when examining how threat actors adapt their methodologies based on previous successes, organizational vulnerabilities, and shifting security landscapes. Effective defense strategies must evolve alongside the increasingly sophisticated tactics and methods employed by various threat actor categories.
Moreover, by categorizing actors according to their primary psychological drivers—whether nation-state geopolitical advantages, hacktivist ideological commitments, or cybercriminal financial incentives—security professionals can anticipate attack vectors with greatly improved precision.
Cross-Domain Security Perspectives
Cross-domain security perspectives, though historically siloed within discrete operational frameworks, increasingly demand convergent analysis approaches to address the polymorphic threat landscape challenging modern enterprises.
Modern security architecture requires integration of unidirectional and bidirectional cross domain solutions, which, when properly implemented through sophisticated hardware-software combinations, enable controlled information exchange while maintaining regulatory compliance. These solutions effectively apply validation to information as it moves between security domains.
Three essential implementation strategies include:
- Deploying data diodes and cryptographic controls that enforce strict unidirectional flow patterns
- Implementing multilevel security architectures with mandatory access controls across varying classification domains
- Establishing continuous monitoring frameworks that validate transfer integrity while identifying potential exfiltration attempts
Organizations seeking innovative cross-domain implementations must balance accessibility requirements with robust security controls, particularly when addressing the complexity inherent in networked environments containing segmented resources.
Create Actionable Resources for Immediate Implementation

Transforming cybersecurity knowledge into practical, implementable resources represents a critical step in achieving content saturation that drives meaningful organizational change. Organizations must distill complex cybersecurity frameworks into digestible, actionable resources that enable swift implementation across various operational domains. Establishing a realistic timeline helps organizations maintain momentum while implementing critical security initiatives and ensures teams can track progress effectively against improvement goals. Effective SEO strategies can enhance visibility for cybersecurity firms, allowing them to reach a broader audience with these actionable resources.
| Implementation Element | Strategic Value | Immediate Actions |
|---|---|---|
| Response Playbooks | Standardizes incident handling | Develop templates based on NIST framework |
| KPI Dashboard | Measures security effectiveness | Implement automated metrics reporting |
| Role Assignment Matrix | Clarifies responsibilities | Map personnel to critical security functions |
When developing these resources, security teams should prioritize alignment with established frameworks, while ensuring actionable implementation steps are clearly defined, measurable, and assigned to responsible stakeholders.
Focus on Emerging Threats and Zero-Day Vulnerabilities
Organizations seeking content dominance in cybersecurity must establish robust zero-day threat intelligence networks, which incorporate threat feeds, industry partnerships, and specialized research teams dedicated to identifying vulnerabilities before widespread exploitation occurs. Enhanced early detection mechanisms, including behavior-based analytics, anomaly detection systems, and AI-driven monitoring solutions, represent critical investments that enable security teams to identify attack signatures not yet cataloged in conventional defense systems.
The urgency for this approach is highlighted by last year’s disclosure of over 30,000 vulnerabilities, marking a significant increase that traditional signature-based detection cannot effectively address. Implementing real-time threat detection capabilities is essential in strengthening the overall security posture against these evolving threats.
Specialized incident response protocols, specifically engineered for zero-day vulnerabilities, should be developed through tabletop exercises that simulate novel attack vectors, thereby ensuring technical teams can rapidly deploy containment strategies when conventional security measures prove insufficient against emerging threats.
Zero-Day Threat Intelligence
The invisible menace of zero-day vulnerabilities represents one of the most formidable challenges in modern cybersecurity landscapes, compelling security professionals to develop increasingly sophisticated detection and mitigation strategies.
Organizations confronting these unpatched security flaws must implement proactive exploit mitigation frameworks that transcend conventional signature-based detection methods, which invariably fail against previously unseen attack vectors. The implementation of comprehensive endpoint security solutions is critical for detecting and neutralizing these threats before they can cause widespread damage.
Effective zero-day intelligence requires:
- Continuous monitoring of behavioral anomalies across network infrastructure, rather than relying solely on known threat indicators
- Integration with real-time threat intelligence feeds from multiple vetted sources
- Implementation of sandboxing technologies that analyze suspicious code execution without risking production environments
Early Detection Mechanisms
While conventional security measures establish foundational protections, sophisticated early detection mechanisms represent the critical frontline defense against the perpetually evolving landscape of emerging threats and zero-day vulnerabilities. Through continuous network traffic analysis, organizations can implement anomaly identification systems that recognize behavioral deviations, which often indicate sophisticated attack patterns before they fully materialize. Organizations must prioritize these systems given the alarming 689% increase in disclosed vulnerabilities over the past six years.
| Detection Approach | Primary Function | Key Advantage |
|---|---|---|
| Behavioral Analysis | Identifies unusual user actions | Catches insider threats |
| Network Traffic Monitoring | Analyzes data flow patterns | Detects lateral movement |
| Machine Learning Integration | Recognizes subtle anomalies | Improves over time |
| Real-Time Alerting | Triggers immediate notification | Enables rapid response |
| Proactive detection | Anticipates attack vectors | Prevents zero-day exploitation |
Specialized Incident Response
Nearly every successful cybersecurity defense strategy must incorporate specialized incident response protocols that address the volatile landscape of emerging threats and zero-day vulnerabilities, which continue to proliferate at unprecedented rates across global networks.
Organizations implementing AI Threat Detection capabilities alongside Cloud Security Strategies are demonstrating enhanced preparedness against Ransomware Evolution and Autonomous Malware Challenges, particularly when these technologies are integrated within Zero Trust Principles framework that validates every access request, regardless of origin. The alarming reality that data exfiltration occurs within the first hour of compromise in nearly 20% of cases underscores the critical need for rapid detection systems.
- Effective Operational Disruption Response requires continuous Threat Intelligence Sharing across industry sectors to maintain visibility into emerging attack vectors.
- Insider Threat Mitigation demands sophisticated behavioral analytics that can distinguish between legitimate activities and malicious actions.
- Advanced Malware Defense necessitates robust Patch Management Tactics with accelerated deployment timelines to address zero-day vulnerabilities.
Build Credibility Through Technical Expertise and Case Studies
Establishing credibility in cybersecurity necessitates a systematic demonstration of technical proficiency, validated through objective credentials and practical application in real-world scenarios. Organizations and professionals within the industry must leverage documented incidents as foundational evidence of their technical expertise, particularly when presenting solutions to complex security challenges that require innovative approaches. Implementing a defense-in-depth strategy provides multiple layers of protection against evolving cyber threats. Moreover, organizations can enhance their market positioning by utilizing data-driven decisions to refine their marketing strategies effectively.
| Credibility Element | Validation Method | Business Impact |
|---|---|---|
| Technical Expertise | Industry Certifications | Enhanced Client Trust |
| Threat Intelligence | Published Research | Proactive Risk Mitigation |
| Incident Response | Documented Case Studies | Reduced Resolution Time |
| Vulnerability Management | Bug Bounty Participation | Decreased Exploit Surface |
| Root Cause Analysis | Post-Mortem Reports | Continuous Improvement |
Optimize for Voice Search and Specific Security Queries

The cybersecurity landscape requires not only demonstrable expertise but also sophisticated content optimization strategies that address evolving search behaviors.
Voice search optimization, which leverages conversational phrases and natural language processing, represents a significant opportunity for cybersecurity content to achieve greater visibility in an increasingly saturated market.
Conversational NLP techniques offer cybersecurity content strategic advantages in today’s voice-driven search ecosystem.
To effectively implement voice search optimization for cybersecurity queries:
- Structure content in question-answer format that mirrors natural speaking patterns, particularly addressing common security concerns such as “What measures protect against ransomware?”
- Utilize structured data markup to enhance search engine comprehension of contextual relevance.
- Incorporate local-specific elements for users seeking “cybersecurity services near me.”
- Optimize content with longer, more conversational phrases since voice inquiries average 29 words compared to the much shorter text-based searches. Additionally, local search queries are crucial as 21% of U.S. consumers use them to find businesses daily.
Establish Thought Leadership in Specialized Security Niches
While generalized cybersecurity content proliferates across digital channels, forward-thinking organizations and professionals must carve distinctive niches within specialized security domains to establish meaningful thought leadership positions.
Specifically, as AI-driven threats accelerate in sophistication, with 17% of cyberattacks projected to employ generative AI by 2027, expertise development through specialized certifications becomes essential for differentiation in the marketplace. Additionally, organizations should prioritize real-time threat detection capabilities to enhance their credibility and effectiveness in addressing evolving security challenges.
Furthermore, establishing industry collaborations and partnerships creates robust ecosystems for knowledge exchange, particularly when addressing emerging challenges like quantum computing vulnerabilities. These challenges require interdisciplinary approaches that combine technical expertise with regulatory compliance knowledge, ultimately positioning organizations as authoritative voices in increasingly complex security landscapes.
The alarming rate of vulnerability-based attacks, which saw a 124% increase in Q3 2024, underscores the importance of developing focused expertise in rapid detection and remediation strategies.
Utilize Visual Content to Simplify Complex Security Concepts
Visual representations of intricate cybersecurity frameworks transform traditionally impenetrable technical concepts into accessible, intuitive knowledge structures that resonate with diverse stakeholders across organizational hierarchies.
Through sophisticated visual storytelling techniques, organizations effectively combat information overload while simultaneously enhancing audience retention and comprehension of critical security measures. Effective visual content significantly improves client engagement with cybersecurity information by accommodating different learning preferences. Additionally, the strategic use of data-rich infographics can effectively communicate complex statistics and trends that are crucial for understanding cybersecurity landscapes.
- Implement data visualization dashboards that translate complex threat intelligence into actionable insights, enabling real-time monitoring and response capabilities.
- Develop thorough infographic design templates that systematically deconstruct advanced persistent threats into recognizable patterns.
- Create interactive visual models that illustrate network vulnerabilities, mapping potential attack vectors across enterprise architecture.
This strategic implementation of visuals not only bridges communication barriers between technical specialists and executive leadership but fundamentally accelerates the learning process when introducing sophisticated security protocols throughout the organization.
Implement Strategic Content Distribution Across Relevant Channels
Strategic deployment of cybersecurity content across multifaceted distribution channels amplifies organizational messaging, transforming isolated security insights into pervasive knowledge assets that penetrate diverse stakeholder ecosystems.
Effective content curation necessitates leveraging social media platforms, industry-specific blogs, webinars, podcasts, and targeted events where security professionals congregate, thereby maximizing audience engagement through multiple touchpoints. Additionally, implementing effective SEO strategies can significantly increase visibility and drive traffic to these valuable resources.
Diversify cybersecurity content across digital channels to create immersive touchpoints where security professionals naturally engage.
With the cybersecurity market expected to reach US$202.98 billion by 2025, distributing compelling content becomes increasingly critical to stand out in this expanding landscape.
Organizations must, when developing distribution frameworks, consider:
- Channel-specific content adaptations
- Collaborative partnerships with industry influencers
- Personalized engagement strategies based on audience segmentation
- Integration of educational resources with storytelling techniques
- Strategic positioning through trusted channel resellers with established market relationships
Overcome Content Saturation with These Ideas Today!
As the cybersecurity landscape continues to evolve amidst overwhelming content proliferation, organizations that strategically implement these ten approaches, while consistently delivering high-value, technically-differentiated content across optimized channels, will establish authoritative market positions. Through methodical audience segmentation, data-driven insights, and visual communication techniques that transform complex security concepts into actionable intelligence, cybersecurity communicators can effectively penetrate the noise barrier, thereby elevating their visibility and influence within the increasingly saturated digital ecosystem.
Frequently Asked Questions
How Do I Measure ROI on Cybersecurity Content Marketing?
Measuring cybersecurity content marketing ROI requires tracking content performance through conversion rates, lead acquisition costs, and engagement metrics. Organizations should implement analytics tools that quantify marketing metrics against security-specific business outcomes.
What Cybersecurity Certifications Best Complement Content Creation?
Certifications like CEH, Security+, and CISSP offer certification benefits for content creation through technical credibility. CISM and OSCP provide specialized knowledge that enables innovative, authoritative cybersecurity content development across various domains.
How Often Should Security Content Be Updated to Remain Relevant?
Security content requires quarterly updates at minimum, with monthly content refreshment strategies recommended for cutting-edge relevance. Audience engagement frequency should align with emerging threat vectors, reflecting the 11-second ransomware attack reality.
Which Cybersecurity Topics Typically Generate Highest Reader Engagement?
Ransomware, cyber-enabled fraud, and AI-powered threats consistently drive highest engagement, with readers seeking innovative approaches to Data Breaches, Incident Response, and Security Awareness aligned with Latest Threats in their industries.
How Can Small Security Teams Compete With Enterprise Content Resources?
Small security teams can leverage niche marketing and targeted messaging to differentiate themselves, focusing on specialized expertise rather than volume. Strategic partnerships and AI-powered content tools amplify their reach despite limited resources.