Do you Really Need Backlinks From Cybersecurity Publications?
In the rapidly evolving cybersecurity landscape, earning backlinks from cybersecurity publications requires strategic precision and demonstrated expertise, not merely basic outreach efforts. Organizations seeking to enhance their digital authority must distinguish themselves through data-driven content assets, specialized technical insights, and cultivated industry relationships. While many security firms struggle with generic content that fails to capture editorial attention, those implementing proven methodologies consistently secure valuable placements, thereby strengthening their domain authority and industry positioning. The following actionable strategies reveal the systematic approach used by successful cybersecurity companies to secure coveted backlinks from tier-one security publications.
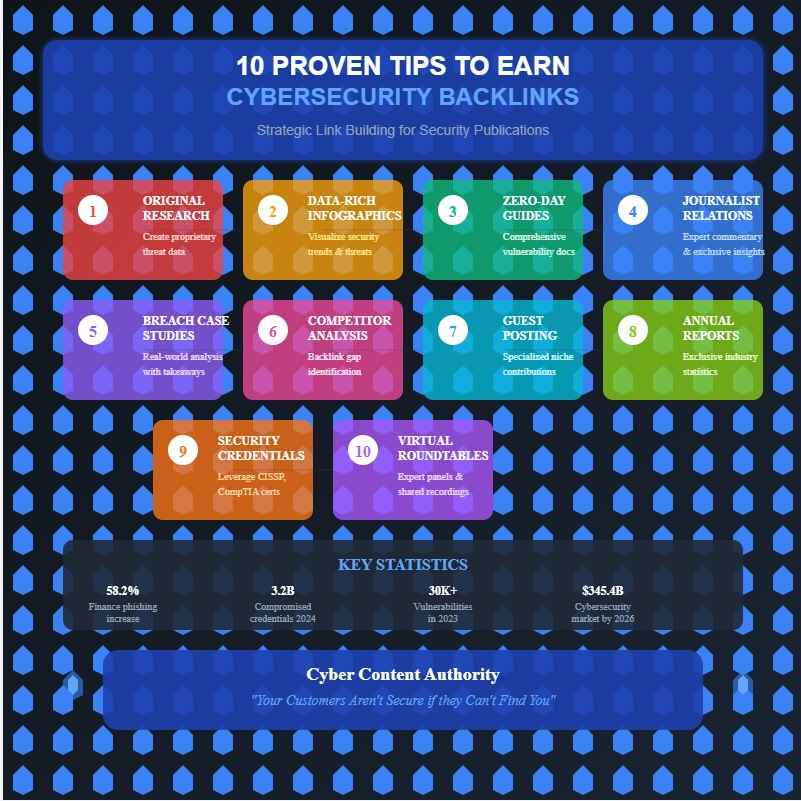
Key Takeaways
- Create original research with proprietary data on emerging cyber threats to attract authoritative backlinks from security publications.
- Develop comprehensive guides on zero-day vulnerabilities that demonstrate expertise and provide valuable industry insights.
- Offer journalists timely, expert analysis during cybersecurity incidents to position yourself as an indispensable media resource.
- Transform complex security threats into visually appealing infographics that publications find shareable and reference-worthy.
- Build strategic relationships with cybersecurity journalists by providing exclusive insights rather than promotional content.
Conduct Original Research on Emerging Cyber Threats

Maneuvering the complex landscape of cybersecurity requires continuous monitoring of evolving threats that proliferate across digital ecosystems.
Organizations seeking authoritative backlinks must develop proprietary research that illuminates the cybersecurity landscape through meticulous data analysis and trend identification, particularly focusing on industry-specific vulnerabilities such as the finance sector’s 58.2% increase in phishing attempts or the 72% attack rate affecting Canadian SMBs.
To establish credibility, researchers should:
- Analyze threat intelligence across multiple sectors
- Document emerging threats with statistical evidence
- Correlate vulnerability trends (30,000+ in 2023) with specific attack vectors
- Compare industry risk profiles against global benchmarks
Additionally, researchers must anticipate the growing challenges presented by zero-trust architectures as perimeter-based security systems become increasingly obsolete in modern threat environments. As noted, 76% of marketers believe that AI can improve search engine rankings, which can enhance the visibility of their research.
Create Data-Rich Infographics That Visualize Security Trends
Transforming complex cybersecurity threats into visually digestible infographics enables security professionals to comprehend intricate attack vectors, vulnerability patterns, and mitigation strategies without wading through dense technical documentation.
When designing these visual assets, the strategic application of color psychology greatly impacts viewer engagement, with blue tones promoting trustworthiness in data representation, red highlighting critical vulnerabilities, and green indicating secured systems or successful countermeasures. Additionally, it’s important to note that over 7 billion searches are conducted on Google daily, highlighting the vast potential audience for cybersecurity content.
Effective security trend visualizations should balance statistical accuracy with intuitive design elements, incorporating clear hierarchical information flows, comparative metrics that benchmark against industry standards, and contextual annotations that guide viewers through technical concepts without requiring specialized knowledge.
Visualizations of zero-trust architecture implementations can be particularly compelling for organizations looking to enhance their security frameworks while transitioning to hybrid work environments.
Simplify Complex Threats
While the cybersecurity landscape grows increasingly intricate with each passing year, organizations must distill complex threat intelligence into digestible formats that facilitate comprehension and decisive action among stakeholders.
The modern cyber threat landscape, characterized by over 3.2 billion compromised credentials in 2024 alone, demands innovative credential security strategies that respond to escalating risks.
Organizations should transform statistical complexity into visual narratives, considering that ransomware attacks have increased by 10% recently, while vulnerability exploits have grown by 12%.
This visualization approach, when coupled with AI-enhanced analysis capabilities, enables security professionals to overcome cognitive barriers that typically impede threat comprehension and response implementation. Companies utilizing these techniques can identify breaches significantly faster, as those leveraging AI in security systems detect breaches 108 days sooner than organizations without such technology.
Color Psychology Matters
The strategic application of color psychology in cybersecurity infographics represents a critical, yet often overlooked dimension of effective security communication that markedly enhances comprehension, retention, and action-taking among diverse stakeholders.
When visualizing complex threat landscapes, strategic color selection transcends mere aesthetics, functioning instead as a sophisticated visual storytelling mechanism that evokes specific color emotions aligned with security messaging priorities.
Additionally, consistent color schemes facilitate rapid pattern recognition, enabling viewers to process multi-layered data regarding emerging threats, such as AI-driven attacks or IoT vulnerabilities, without cognitive overload.
With the global cybersecurity market projected to reach $345.4 billion by 2026, infographics that effectively communicate security trends are becoming increasingly valuable.
Consequently, infographics leveraging appropriate color psychology transform otherwise intimidating statistical information into accessible, memorable, and actionable security intelligence that resonates across technical and non-technical audiences alike.
Develop Comprehensive Guides on Zero-Day Vulnerabilities
As organizations face increasing threats from previously unknown security flaws, developing extensive guides on zero-day vulnerabilities becomes essential for cybersecurity professionals seeking to fortify their defensive posture against emerging threats. Through systematic zero day discovery processes and proactive vulnerability patching strategies, organizations can effectively mitigate risks before exploitation occurs. Recent exploits like those by Marbled Dust group targeting Indian enterprises demonstrate the critical need for comprehensive vulnerability management.
| Vulnerability Aspect | Impact Level | Mitigation Priority |
|---|---|---|
| Enterprise Platforms | Critical | Immediate |
| Remote Code Execution | Severe | Within 24 Hours |
| Information Disclosure | Moderate | Within 48 Hours |
| Privilege Escalation | High | Within 72 Hours |
When crafting extensive guides, attention must focus on the increasing sophistication of threat actors, particularly their shift toward enterprise platforms, which now represent 44% of targets.
Build Relationships With Cybersecurity Journalists Through Expert Commentary
Security professionals who establish strategic relationships with cybersecurity journalists, offering exclusive insights that go beyond commonly available information, can greatly enhance their backlink profile while positioning themselves as trusted authorities in the field.
Through providing timely analysis of emerging threats, zero-day vulnerabilities, and industry developments, experts create valuable opportunities for journalists who constantly seek credible sources that can contextualize complex technical issues for their audiences. This relationship building is especially important given that varied legal frameworks globally often fail to adapt to technological changes, creating an environment where journalistic work requires expert guidance on emerging digital threats.
These relationships, when cultivated through consistent delivery of accurate, actionable commentary rather than promotional content, ultimately yield higher-quality media mentions and backlinks that carry substantial domain authority and relevance within the cybersecurity ecosystem.
Offer Exclusive Insights
Numerous cybersecurity professionals overlook the strategic advantage of offering exclusive insights to journalists, which, when executed properly, can establish authoritative industry positioning while simultaneously generating valuable backlinks from reputable publications.
When security experts share proprietary research findings or cutting-edge cybersecurity innovations, journalists receive contextually valuable content unavailable elsewhere, thereby increasing the likelihood of citation and attribution.
This approach, requiring deliberate cultivation of relationships through consistent delivery of high-quality, data-driven analysis rather than generic commentary, transforms the expert into a trusted resource. Original research can yield exceptional results as it has proven to be a powerful strategy for generating natural backlinks from trusted publications.
Provide Timely Analysis
Providing timely analysis represents the cornerstone of meaningful journalist relationships, particularly when cybersecurity incidents demand immediate expert interpretation that journalists, working under tight deadlines, cannot develop independently.
Organizations that monitor emerging threats and develop rapid, contextual insights position themselves as invaluable resources within the media ecosystem. This, when executed strategically while respecting responsible disclosure protocols, transforms into substantial earned media coverage and authoritative backlinks. Establishing multiple communication channels across departments enhances your ability to deliver expert commentary quickly and effectively to journalists when incidents occur.
For maximum impact during incident response scenarios, cybersecurity professionals should:
- Structure analysis within established frameworks
- Contextualize incidents against broader industry trends
- Offer data-driven perspectives that illuminate technical complexities
- Maintain transparency while adhering to timely reporting standards
Document Real-World Breach Case Studies With Actionable Takeaways
When organizations analyze documented case studies of notable data breaches, they gain invaluable insights that can greatly improve their security posture and incident response capabilities.
The real-world impact of incidents, such as the VeriSource Services breach affecting 4 million individuals or the Hertz Corporation compromise exposing 1 million records, demonstrates the critical necessity of thorough breach analysis.
Major data breaches at VeriSource and Hertz reveal why thorough breach analysis is no longer optional for organizations.
To leverage these case studies effectively, security professionals should:
- Identify common vulnerability patterns
- Evaluate third-party security risks
- Implement robust incident response protocols
- Conduct regular security audits
Case studies reveal that organizations implementing proactive security measures, including employee education and systematic technology updates, greatly reduce breach probability and severity. Many breaches occur through exploited vulnerabilities in systems, as evidenced by the Microsoft Exchange server attack that affected 30,000 US organizations in 2021.
Analyze Competitor Backlink Profiles to Identify High-Value Opportunities

Effective competitor backlink analysis begins with a thorough gap evaluation, which, when conducted through specialized tools such as Semrush’s Backlink Gap Tool or Ahrefs’ Link Intersect, reveals domains linking to competitors but not to one’s own site.
Through meticulous examination of these backlink profiles, cybersecurity firms can identify high-value opportunities that align with their content strategy, prioritizing authoritative sources like government agencies, educational institutions, and respected industry publications. Understanding the quality and relevance of backlinks is crucial, as this knowledge provides insights into competitors’ SEO effectiveness rather than simply pursuing high Domain Authority scores. Additionally, employing a robust strategy can help leverage the fact that backlinks are one of Google’s top three ranking factors, enhancing overall site visibility and authority.
Gap Analysis First
Strategic intelligence in the cybersecurity backlink landscape begins with thorough competitor analysis, which, when executed meticulously, reveals invaluable opportunities other organizations have either overlooked or failed to capitalize upon.
When implementing backlink strategies, organizations must deploy extensive tools such as Ahrefs, Moz, and SEMrush to audit competitors’ profiles, examining not merely quantity but the qualitative dimensions of their link portfolios.
Through rigorous competitor analysis, cybersecurity firms can identify publication patterns, anchor text diversity, and domain authority metrics that signal high-value targets. Research shows that high-ranking Google pages typically have substantially more backlinks than lower-ranked pages, underscoring the critical importance of strategic link acquisition.
In addition, this systematic evaluation enables organizations to discern effective industry-specific approaches, thereby informing strategic decisions that elevate visibility within the cybersecurity ecosystem.
Identify Link Opportunities
Thorough analysis of competitor backlink profiles reveals a treasure trove of high-value opportunities that organizations can strategically leverage to enhance their cybersecurity publication presence. By systematically examining how industry leaders secure placements, companies can identify domains with high domain authority, social media integration capabilities, and content preferences. Implementing robust verification processes similar to reCAPTCHA can strengthen a website’s security credibility when seeking backlinks from cybersecurity publications.
| Strategy | Implementation Approach |
|---|---|
| High-Authority Domains | Target publications linking to multiple competitors |
| Guest Blogging | Analyze competitor author profiles for placement patterns |
| Resource Pages | Identify security directories featuring competitor content |
| Influencer Outreach | Map relationships between publications and thought leaders |
| Broken Link Building | Monitor competitor link degradation for replacement opportunities |
Furthermore, organizations should prioritize opportunities based on domain relevance, backlink quality, and potential traffic generation, while developing specialized content that addresses publication-specific requirements to maximize acceptance probability.
Outrank Competitor Content
Analyzing competitor backlink profiles yields actionable intelligence that organizations can leverage to create superior content strategies, thereby outperforming their cybersecurity industry rivals.
Through meticulous competitor keyword analysis, companies can identify high-authority domains linking to competitive content and develop targeted outreach campaigns addressing content gaps within the cybersecurity landscape.
Implementing a thorough backlink diversity strategy, which examines both the quantity and quality of competitors’ inbound links, enables organizations to strategically allocate resources toward creating more substantive, technically superior content.
Additionally, by analyzing anchor text patterns and link acquisition timelines, cybersecurity firms can craft content that specifically addresses underdeveloped topics, ultimately attracting higher-quality backlinks from authoritative industry publications.
Tools like Semrush Backlink Gap Tool allow cybersecurity companies to effectively compare their site’s backlinks against competitors and identify untapped link-building opportunities that can strengthen their domain authority in the industry.
Contribute Guest Posts Focused on Specialized Security Niches
Why do generic cybersecurity articles fail to generate quality backlinks when specialized, niche-focused content consistently outperforms in editorial acceptance rates?
Security publications actively seek contributions demonstrating profound expertise in targeted domains, particularly those addressing emerging challenges in secure coding and threat modeling. Contributors who cultivate specialized authority, rather than producing generalist content, establish themselves as indispensable resources for discerning editors seeking substantive analysis. The education sector, which faced more cyberattacks than any other industry in Q2 2024, represents a particularly valuable niche for specialized content development.
- Analyze proprietary data from industry research to provide insights unavailable elsewhere
- Document case studies from recent attacks, focusing on prevention methodologies
- Incorporate visualization elements that transform complex vulnerabilities into comprehensible frameworks
When approaching publications, practitioners should emphasize their unique perspective within specific security domains, thereby positioning themselves as subject matter experts whose contributions merit citation and sharing.
Produce Annual Industry Reports With Exclusive Statistics
Nearly 83% of cybersecurity publications actively seek data-rich industry reports containing exclusive statistics that cannot be found through conventional research channels. Organizations that produce extensive annual reports, which spotlight emerging threats and provide exclusive insights into the cybersecurity landscape, gain significant backlink opportunities from high-authority publications seeking to reference authoritative data sources. The growing impact of geopolitical tensions on cybersecurity makes these reports particularly valuable to publications covering international security developments. Additionally, 63% of all shopping begins online, underscoring the importance of credible data for influencing purchasing decisions in the cybersecurity sector.
| Report Focus | Backlink Potential | Actionable Recommendations |
|---|---|---|
| Cybercrime Cost Projections | Very High | Develop proprietary cost metrics |
| Breach Response Times | High | Include industry-specific benchmarks |
| GenAI Security Risks | Very High | Feature case studies with solutions |
| Remote Work Vulnerabilities | Medium | Offer preventative frameworks |
Successful reports require thorough research methodologies, collaboration with recognized experts, and global statistical analysis to establish credibility within the cybersecurity community.
Leverage Security Certifications and Credentials in Outreach Campaigns

Showcasing industry-recognized security certifications represents a powerful strategy for cybersecurity professionals seeking to establish credibility and generate valuable backlinks through targeted outreach campaigns.
By strategically highlighting credentials such as CISSP or CompTIA Security+, which command an average global salary premium of $91,727, professionals can considerably enhance credential visibility while positioning themselves as authoritative voices within specialized security domains. This is especially important as link quality has become a top priority in successful link-building strategies.
Security certifications like CISSP transform professionals into industry authorities while commanding substantial salary premiums.
- Certification impact extends beyond personal advancement, opening doors to publication contributions, speaking engagements, and collaboration opportunities.
- Vendor-specific certifications from industry leaders like Fortinet and Google demonstrate specialized expertise that publication editors actively seek.
- Strategic credential display in outreach materials increases response rates by validating expertise before initial contact is established.
Incorporating advanced certifications like the Offensive Security Certified Professional (OSCP) can significantly strengthen your pitch by demonstrating practical hands-on penetration testing skills that publications value for their authentic security insights.
Host Virtual Roundtables With Industry Experts and Share the Recordings
Building upon the credential-based outreach strategies, virtual roundtables represent an exceptionally potent mechanism for cybersecurity professionals to generate high-quality backlinks while simultaneously establishing thought leadership within specialized security communities.
Organizations implementing this approach should focus on assembling panels of recognized subject matter experts to discuss prevailing cybersecurity trends, ensuring high-quality recording production that participants will enthusiastically share.
In addition, structuring these sessions with interactive components, such as moderated Q&A segments or breakout discussions, considerably enhances engagement metrics and increases the likelihood of content distribution across authoritative platforms. Offering attendees incentives like gift card rewards can significantly boost participation, as demonstrated by successful events like the DG Technology roundtable.
Expert collaborations of this nature, when properly optimized with relevant keywords and distributed through multiple channels, create natural backlink opportunities through reference citations and industry recognition.
What Did We Learn About Securing Backlinks From Cybersecurity Publications?
Securing backlinks from cybersecurity publications demands a strategic approach that integrates original research, relationship cultivation, and authoritative content development, which, when executed systematically, establishes one’s organization as an industry thought leader. By implementing these ten methodologies, companies can effectively navigate the competitive landscape of cybersecurity content marketing, thereby enhancing domain authority, increasing referral traffic, and solidifying their position within the cybersecurity ecosystem through credible third-party endorsements.
Frequently Asked Questions
How Long Should I Wait Before Following up With Cybersecurity Journalists?
Ideal follow up timing with cybersecurity journalists typically ranges from 3-5 business days. This balanced approach respects their workflow while maintaining momentum in journalist engagement during fast-evolving security news cycles.
Which Cybersecurity Publications Offer the Highest Domain Authority for Backlinks?
Among top cybersecurity publications, Cyber Magazine offers the highest domain authority at 37, followed by Cybersecurity Magazine at 31. Implementing targeted backlink strategies with these platforms maximizes SEO impact for innovative security content.
How Can Smaller Companies Compete Against Established Security Vendors for Backlinks?
Smaller companies can leverage niche expertise and targeted outreach to compete against established security vendors, focusing on specialized topics where they demonstrate exceptional knowledge rather than battling for broader, more competitive keywords.
What Content Formats Perform Best for Mobile Cybersecurity Audiences?
Mobile-friendly designs with short paragraphs and bold headings excel alongside engaging visual content like infographics and interactive checklists. Video demonstrations and downloadable security resources consistently drive higher engagement among mobile cybersecurity audiences.
Should Technical Cybersecurity Content Be Gated or Freely Accessible for Backlinks?
Technical cybersecurity content performs best ungated for maximizing backlinks, though selective gating of advanced resources can balance lead generation with audience engagement while maintaining SEO benefits and industry credibility.


