How Do You Deal with High Competition in Cybersecurity SEO?
The cybersecurity SEO landscape presents formidable challenges that require strategic navigation beyond conventional approaches. In today’s environment of high competition in cybersecurity SEO, organizations specializing in security solutions frequently encounter saturated SERPs dominated by established industry leaders, government resources, and technical publications. Consequently, capturing valuable SERP real estate demands a methodical framework that combines technical precision with content authority, while simultaneously addressing the nuanced search behaviors of security professionals and decision-makers. What distinguishes successful cybersecurity SEO strategies from ineffective ones lies in the systematic implementation of specialized tactics tailored to this complex vertical.
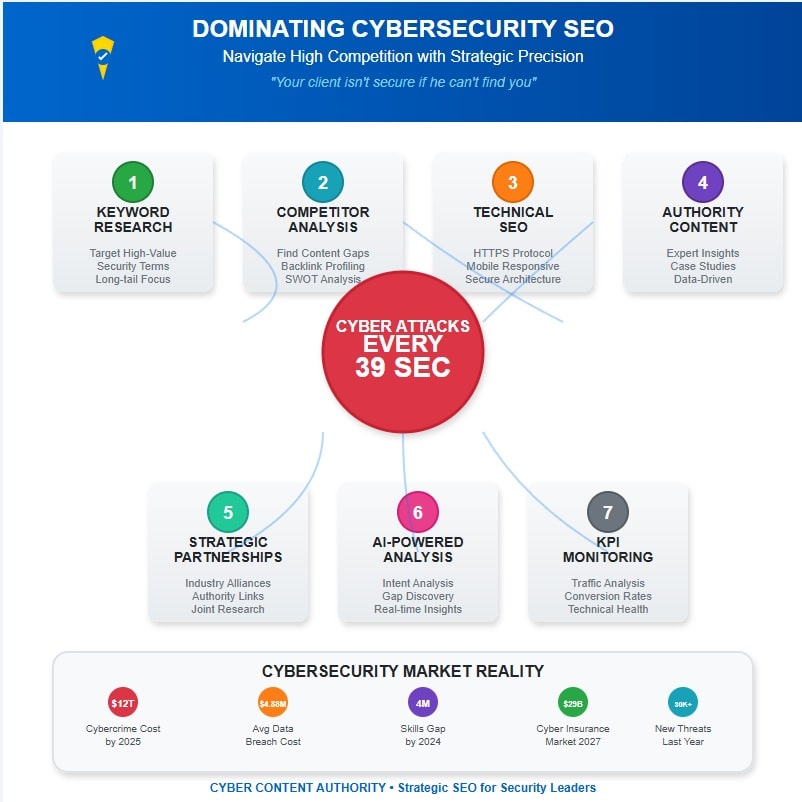
Key Takeaways
- Conduct strategic keyword research to identify high-value terms that target specific cybersecurity niches and user intent.
- Perform comprehensive competitor analysis to find content gaps and differentiate your cybersecurity expertise.
- Implement robust technical SEO foundations including secure architecture, HTTPS, and mobile optimization for credibility.
- Build authority through data-driven content that addresses security vulnerabilities and includes case studies proving implementation efficacy.
- Develop strategic partnerships with security vendors and industry associations to create valuable backlink opportunities.
The Current State of Competition In Cybersecurity SEO

While the cybersecurity market continues to experience unprecedented growth, the competitive landscape for search engine optimization within this sector has intensified dramatically, creating both challenges and opportunities for industry participants.
The current challenges facing cybersecurity SEO professionals stem primarily from algorithm volatility, requiring constant adaptation to emerging trends in search behavior. With cyberattacks occurring every 39 seconds, organizations need content that addresses both immediate threats and long-term security planning. Organizations maneuvering this space must contend with increasingly saturated keyword battlegrounds, particularly for high-value terms related to threat protection, compliance solutions, and enterprise security services. Additionally, SEO investments yield long-term ROI, providing ongoing value beyond initial implementation.
As regulatory frameworks evolve across jurisdictions, content strategies must simultaneously address technical accuracy, educational value, and conversion optimization to maintain visibility.
Identifying High-Value Keywords in the Security Sector
The foundation of effective cybersecurity SEO strategy rests upon the meticulous identification and strategic deployment of high-value keywords that align with both user intent and business objectives. Through thorough keyword discovery processes, security firms can uncover terms that demonstrate commercial intent, while simultaneously addressing specific pain points across the cybersecurity landscape. Properly mapping keywords to the appropriate stages of the buyer journey helps maximize content relevance and conversion potential. Additionally, understanding the importance of industry-specific terms can significantly enhance the targeting of your audience.
| Intent Type | Example Keywords | Conversion Potential |
|---|---|---|
| Informational | “ransomware prevention guide” | Low-Medium |
| Commercial | “compare endpoint protection solutions” | Medium-High |
| Transactional | “buy enterprise security platform” | High |
| Niche-Specific | “HIPAA-compliant security for healthcare” | Very High |
| Threat-Focused | “AI-powered phishing protection” | Medium-High |
Effective niche targeting requires analyzing both search volume and competition metrics, prioritizing long-tail keywords that demonstrate specific purchase intent within specialized cybersecurity domains.
Competitive Analysis: Finding Your Cybersecurity SEO Edge
How effectively does a cybersecurity company understand its competitive landscape before attempting to dominate search results?
In today’s saturated marketplace, where competitors vie for the same high-value keywords, extensive competitor analysis has become the cornerstone of strategic differentiation. This enables organizations to identify exploitable gaps while capitalizing on emerging market trends that others have overlooked. Understanding both direct and indirect competitors is essential for developing targeted SEO strategies that address the full competitive landscape. Monitoring engagement rates across various content formats can provide insights into how competitors are resonating with their audience, further informing your SEO approach.
To gain competitive advantage, organizations should implement a three-pronged approach:
- Deploy advanced SEO tools (Semrush, Ahrefs) for backlink profiling
- Conduct SWOT analyses of direct competitors’ content strategies
- Evaluate user experience metrics across competitive websites
Thorough competitive analysis transforms abstract SEO concepts into actionable intelligence. It provides the foundation for sustainable competitor differentiation.
Technical SEO Foundations for Security-Focused Websites

Security-focused websites require meticulous attention to technical SEO foundations, particularly when cybersecurity companies must simultaneously demonstrate their expertise while implementing robust security measures in their own digital infrastructure.
Through proper keyword optimization integrated with secure architecture principles, organizations can establish credibility within the competitive cybersecurity landscape, while search engines recognize both relevance and trustworthiness, thereby improving visibility among target audiences seeking protection solutions. Implementing strong security protocols is essential not only for protecting website visitors but also for maintaining favorable search engine rankings. Additionally, ensuring website speed optimization plays a pivotal role in retaining users and enhancing the overall experience.
- Implement HTTPS protocol with proper SSL certification, ensuring all traffic remains encrypted while simultaneously improving search rankings through Google’s security-focused algorithm preferences.
- Develop mobile-responsive designs with minimized JavaScript vulnerabilities that enhance user experience while demonstrating technical competence.
- Create XML sitemaps and proper canonicalization structures to facilitate efficient crawling while preventing potential security gaps in site architecture.
Creating Authority Content That Converts Security Professionals
Authority Building in cybersecurity demands integration of statistical impact analysis, with projections indicating cybercrime costs approaching $12 trillion by 2025, alongside technical depth that establishes credibility. Effective integration of content strategies ensures that messaging resonates with both security professionals and organizational objectives.
Content Marketing strategies must pivot toward solution-oriented formats that address the $4.88 million average data breach cost, incorporating case studies that demonstrate implementation efficacy, particularly as cyber insurance premiums surge toward $29 billion by 2027, thereby converting security professionals through demonstrated expertise rather than conventional marketing rhetoric.
While traditional marketing approaches often fall short in the cybersecurity sector, creating authoritative content that resonates with security professionals requires a sophisticated understanding of both technical vulnerabilities and the psychological drivers that influence high-stakes purchasing decisions. The persistent skills gap of four million cybersecurity professionals expected by 2024 further necessitates content that educates while marketing.
Building Backlink Strategies Specific to Cybersecurity
Establishing strategic industry partnerships represents a cornerstone approach for cybersecurity firms seeking to develop authoritative backlink profiles. Collaborations with recognized security vendors, research institutions, and industry associations often yield high-value linking opportunities that carry significant domain authority. The acquisition of these authority links requires methodical outreach to cybersecurity-specific platforms, including threat intelligence portals, information security forums, and compliance resource hubs, where contextually relevant content can attract natural citations from established industry sources.
Effectively identifying unlinked brand mentions using Brand Monitoring tools can significantly improve backlink acquisition rates for cybersecurity companies operating in competitive niches. Furthermore, developing comprehensive guides on emerging threats can serve as a valuable resource that attracts backlinks from credible sources. When executed properly, these targeted backlink strategies not only enhance search visibility but also position cybersecurity companies as credible thought leaders within specialized security communities. This creates a virtuous cycle of authority development and improved SERP performance.
Strategic Industry Partnerships
The cybersecurity landscape presents unique opportunities for building powerful backlink profiles through strategic industry partnerships, which, when implemented methodically, can simultaneously elevate domain authority while establishing critical trust signals for search engines.
Through deliberate cybersecurity networking with software vendors, industry associations, and government bodies, organizations can leverage partnership benefits that extend beyond mere link acquisition to include content syndication and audience expansion.
- Develop joint research initiatives or whitepapers with established security organizations, ensuring cross-promotion across both entities’ digital properties.
- Participate actively in industry consortiums that provide member listings with dofollow backlinks.
- Create co-branded webinars or interactive tools that naturally generate citations from industry publications.
With cybercrime financial impacts reaching an average of 1.3 million dollars in lost business for companies experiencing data breaches, partnership-based content strategies become increasingly valuable for establishing authority in the industry.
Authority Link Acquisition
Effective authority link acquisition in the cybersecurity sector requires a multifaceted approach that leverages industry-specific opportunities, technical credibility markers, and specialized content assets designed to attract high-value backlinks from authoritative domains.
When pursuing backlink strategies, cybersecurity firms must prioritize link quality over quantity, focusing on authoritative industry publications, security forums, and academic institutions that signal relevance to search algorithms.
Additionally, content relevance becomes paramount when developing linkable assets, such as vulnerability research reports, threat intelligence briefings, and technical white papers, which naturally attract citations from reputable sources within the ecosystem. As demonstrated in Malwarefox’s case study, securing high-quality links from relevant IT and cybersecurity platforms led to dramatic improvements in keyword rankings and overall online visibility.
Leveraging AI Tools for Advanced Keyword Research
Why has artificial intelligence emerged as a transformative force in cybersecurity SEO keyword research, revolutionizing how professionals identify and leverage high-value search terms?
AI-powered analysis transforms vast data into actionable intelligence, accelerating cybersecurity decision-making through real-time competitive insights.
Through AI-Driven Insights, organizations can now analyze vast datasets instantaneously, enabling strategic decision-making based on real-time competitive intelligence rather than outdated information. In addition, Google’s search engine market share facilitates User Intent Analysis, allowing cybersecurity marketers to understand the underlying motivations driving search queries, thereby creating content that precisely addresses potential clients’ security concerns. Tools like Semrush offer granular data including SERP features that enhance keyword research effectiveness for cybersecurity professionals.
- Implement long-tail keyword identification to target specific cybersecurity niches
- Utilize content gap analysis to discover untapped market opportunities
- Deploy search volume and competition level assessment to prioritize winnable keyword battles
Balancing Technical Accuracy With Search Intent

When crafting content for cybersecurity SEO, professionals must navigate the delicate balance between maintaining technical precision and satisfying the underlying intent behind user searches, as this equilibrium directly impacts both SERP rankings and conversion potential. Effective security practices, including properly configured SSL/TLS certificates, are essential for establishing user trust.
Effectively, the convergence of technical accuracy and search intent necessitates a structured content strategy that employs expert insights delivered in accessible language, thereby enabling complex cybersecurity concepts to resonate with both search algorithms and human readers. In addition, the natural integration of targeted keywords, enhancement of navigational UX elements, and alignment of technical SEO practices with user expectations creates a framework wherein technical validity never sacrifices relevance to search intent. Implementing secure website practices with SSL certificates contributes significantly to both user trust and SEO performance, as security is a key ranking factor in Google’s evaluation system.
Measuring Success: KPIs for Cybersecurity SEO Campaigns
Quantifiable performance indicators serve as the cornerstone for evaluating cybersecurity SEO campaign effectiveness, allowing organizations to systematically assess their digital visibility while simultaneously monitoring security posture in an increasingly threat-dense online landscape.
Strategic KPI deployment enables security firms to benchmark performance where technical precision meets search prominence, fueling targeted acquisition.
Through rigorous KPI implementation, security-focused enterprises can establish performance benchmarks that align technical accuracy with search visibility, ultimately driving qualified traffic and conversions.
- Organic Traffic Analysis – Track visitor growth patterns during normal operations and security events, identifying correlations between content adjustments and traffic fluctuations. Implement analytics that show historical data progression to enable evidence-based decisions in SEO strategy and content development.
- Conversion Rate Optimization – Measure cybersecurity page performance across lead generation metrics, prioritizing security content that drives measurable business outcomes.
- Technical Health Monitoring – Implement continuous assessment of page speed metrics, SSL status, and security-related ranking factors that impact both user experience and search visibility.
Future-Proofing Your Cybersecurity SEO Strategy
Building upon established performance metrics, forward-thinking cybersecurity organizations must now anticipate the evolutionary trajectory of both search algorithms and threat landscapes, thereby constructing adaptive SEO frameworks capable of maintaining visibility regardless of technological shifts or emerging vulnerabilities. With the significant increase of over 30,000 vulnerabilities disclosed last year alone, cybersecurity content must directly address these emerging threats to maintain relevance. Companies should ensure that their claims are grounded in substantial, verifiable evidence to reinforce consumer trust and credibility.
Organizations embracing content adaptability through AI-powered threat intelligence positioned within extensive, regulation-compliant frameworks will maintain competitive advantage, while those failing to incorporate emerging security trends into their content strategy risk obsolescence as search algorithms increasingly prioritize demonstrated expertise over keyword optimization.
| Strategic Element | Implementation Approach | Risk Awareness Factor |
|---|---|---|
| AI Integration | Deploy predictive analytics | High vulnerability detection |
| Content Adaptability | Dynamic topic modeling | Regulatory compliance |
| Zero-Trust Content | Regular expert validation | Misinformation prevention |
| Semantic Optimization | Entity relationship mapping | Algorithm-proof structure |
Learn to Navigate Competition in Cybersecurity SEO and Come Out On Top!
Steering through the complex landscape of cybersecurity SEO demands a multifaceted approach that integrates technical optimization, authoritative content creation, and strategic keyword targeting. By implementing the thorough framework outlined in this guide, organizations can effectively differentiate their digital presence, despite intense competition in Cybersecurity SEO. Success ultimately hinges on maintaining adaptability while rigorously measuring performance across established KPIs, thereby securing sustainable visibility in an increasingly sophisticated marketplace.
Frequently Asked Questions
How Do Cybersecurity Algorithm Updates Differ From General Google Updates?
Cybersecurity algorithm updates feature specialized algorithm nuances targeting security-related content accuracy, while general Google updates address broader search quality. Cybersecurity updates may require higher update frequency to combat emerging digital threats effectively.
What Certifications Should Content Writers Have for Cybersecurity SEO?
Content writers specializing in cybersecurity SEO benefit from certification importance through Google Analytics, HubSpot SEO, CompTIA Security+, and digital marketing credentials that establish authoritative content credentials in this technical niche.
How Often Should Security-Focused Landing Pages Be Refreshed?
Security-focused landing pages should be refreshed quarterly, with more frequent updates for emerging threats. Fresh content maintains relevance, boosts search rankings, and enhances user engagement in this rapidly evolving digital landscape.
Can Competitor Security Vulnerabilities Be Ethically Leveraged for SEO?
Leveraging competitor vulnerabilities for SEO crosses ethical boundaries. Organizations should instead focus on legitimate competitive analysis and ethical hacking practices to strengthen their own security posture, indirectly enhancing SEO through demonstrated expertise.
How Do GDPR Compliance Pages Affect Overall Domain Authority?
GDPR compliance pages positively influence domain authority when implemented transparently. Effective compliance strategies demonstrate, while poor GDPR implementations risk search penalties. The broader GDPR implications extend beyond compliance to overall site credibility.



