SEO Assets: Using Resource Pages to Gain Links
Cybersecurity organizations seeking competitive advantages must recognize how resource pages function as strategic SEO assets, particularly when market visibility remains critical for establishing thought leadership. In today’s threat-dense digital landscape, extensive security resource collections—featuring technical whitepapers, vulnerability databases, and compliance frameworks—serve as powerful link magnets when expertly optimized and promoted across industry channels. Despite their proven efficacy, many security firms underutilize this approach, missing opportunities to elevate domain authority while competitors secure valuable backlinks through similar content initiatives. The subsequent analysis explores precisely how using resource pages to gain links can be implemented for maximum impact.
Key Takeaways
- Develop resource pages featuring original cybersecurity research and interactive assessment tools to establish authority and attract high-quality backlinks.
- Include downloadable security templates aligned with industry standards to enhance domain credibility and streamline compliance assistance.
- Optimize resource pages with proper schema markup, mobile responsiveness, and security trust indicators for improved technical SEO.
- Partner with cybersecurity influencers and conference participants to build strategic relationships for valuable backlink opportunities.
- Monitor SEO impact through referral traffic metrics, domain authority improvements, and keyword ranking gains tied to resource page performance.
Understanding the Power of Resource Pages in Cybersecurity SEO

Authority, in the competitive landscape of cybersecurity marketing, emerges as a fundamental currency that transforms digital visibility into tangible business outcomes.
Resource pages, which thoroughly aggregate topic-specific assets with ideal resource diversity, function as digital hubs that simultaneously serve users and signal expertise to search algorithms. By incorporating original research on emerging threats, these pages can enhance their credibility and relevance to current industry challenges.
When strategically implemented, these curated collections leverage link relevance to establish the domain as an authoritative reference point within the cybersecurity ecosystem, thereby generating natural backlink acquisition from industry publications, educational institutions, and adjacent sectors seeking reliable information sources. Well-optimized resource pages provide cost-effective marketing solutions compared to paid advertising while delivering sustained visibility and credibility in the cybersecurity sector.
Identify High-Value Link Opportunities Within the Security Sector
Where do cybersecurity professionals identify the most strategically valuable link opportunities that yield substantial SEO benefits while reinforcing domain authority?
Methodical landscape analysis reveals resources that enhance visibility while building audience credibility when strategically leveraged.
Through methodical analysis of the security landscape, organizations can uncover resources that, when leveraged appropriately, provide substantial visibility enhancements while establishing credibility among the targeted audience. The success of Malwarefox demonstrates that focusing on securing high-quality backlinks from relevant IT and cybersecurity platforms can dramatically improve SEO performance. Additionally, analyzing engagement metrics from existing partnerships can help identify the most effective strategies for link-building.
- Industry influencers with substantial engagement metrics offer partnership opportunities that translate into authoritative backlinks.
- Educational institutions with cybersecurity programs provide high domain authority links.
- Security conferences and events present networking opportunities for strategic relationship development.
- Competitor analysis reveals existing gaps in resource coverage, allowing for differentiated positioning.
Creating Compelling Resource Content That Attracts Backlinks
Building effective cybersecurity resource pages requires offering substantive, value-driven content that addresses critical industry challenges, incorporates authoritative sources, and provides actionable solutions for security professionals. Additionally, a well-structured resource page can significantly enhance SEO visibility, ensuring that your content reaches a broader audience and attracts valuable backlinks.
Through the strategic implementation of interactive tools, such as threat assessment calculators or vulnerability scanners, organizations can transform static information into engaging experiences that naturally attract high-quality backlinks from industry websites and forums.
Additionally, the inclusion of downloadable materials, including incident response templates, security policy frameworks, and compliance checklists, establishes the resource page as an authoritative reference point within the cybersecurity ecosystem, thereby encouraging spontaneous link-building from practitioners seeking reliable information sources. Following industry leaders like Wiz and UpGuard, incorporating calming blue colors in your resource page design helps create an atmosphere of trust and security that visitors instinctively associate with reliable cybersecurity information.
Value-Driven Cybersecurity Resources
Creating compelling cybersecurity resources that naturally attract high-quality backlinks requires a deliberate approach focused on delivering exceptional value to both users and potential linking domains.
Successful resource pages establish a strong value proposition through thorough, authoritative content that addresses specific pain points within the cybersecurity ecosystem, while leveraging industry partnerships to enhance credibility and expand reach. Long-form cybersecurity content with comprehensive technical details receives significantly more backlinks than shorter posts.
- Develop proprietary research reports analyzing emerging threats and vulnerabilities
- Create interactive assessment tools that evaluate organizational security postures
- Maintain thorough glossaries of technical terminology with expert annotations
- Establish curated collections of vetted open-source security tools with implementation guides
Interactive Tools Attract Links
Interactive tools, strategically developed to solve real-world cybersecurity problems, represent one of the most potent link acquisition assets in a thorough SEO strategy.
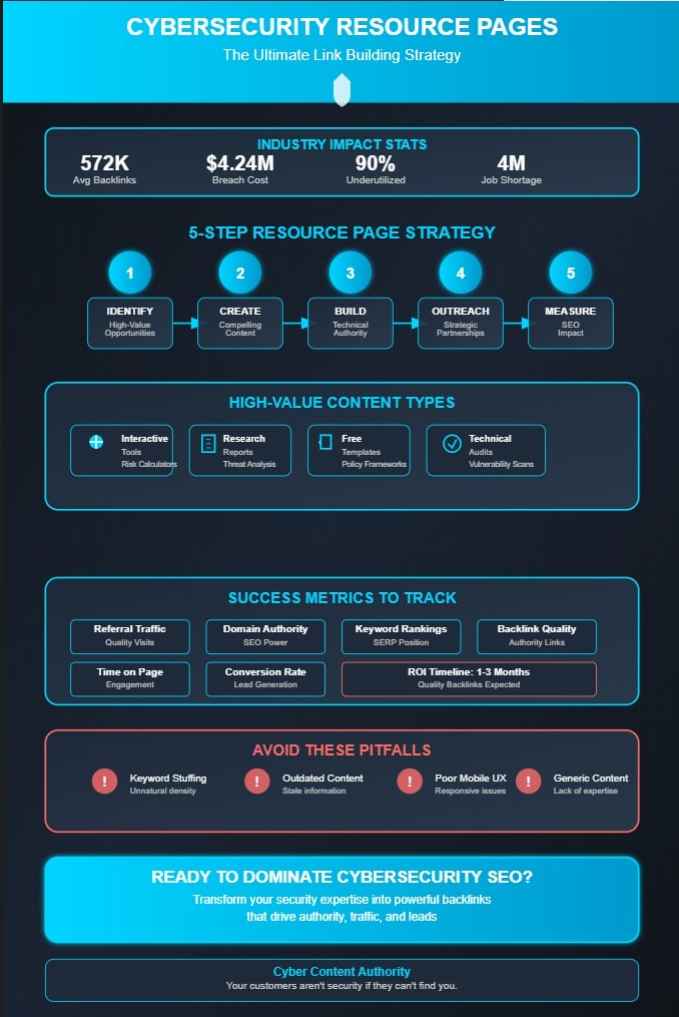
The implementation of risk calculators and interactive quizzes creates measurable engagement improvements, with statistics revealing cybersecurity startups average 572,665 backlinks when utilizing these dynamic assets.
These interactive elements, which must prioritize utility over mere novelty, simultaneously reduce bounce rates while increasing time-on-site metrics—factors search engines interpret as indicators of content value.
Interactive resource pages that educate users about the financial implications of data breaches can be particularly compelling, especially considering the average data breach now costs organizations approximately $4.24 million to remediate.
In addition, when designed with intuitive interfaces and mobile responsiveness, these tools generate significant social sharing, attract citations from authoritative industry sources, and encourage repeated visits through bookmarking, thereby establishing sustainable link-building momentum.
Free Templates Build Authority
Free cybersecurity templates, strategically deployed as accessible downloads on resource pages, fundamentally transform link acquisition strategies while simultaneously establishing domain authority in competitive digital landscapes.
Organizations that integrate customizable, thorough templates aligned with industry standards cultivate authoritative positioning, which, when properly optimized with relevant keywords, attracts high-quality backlinks from educational institutions, security professionals, and corporate entities. Implementing comprehensive templates for security policy creation helps businesses prepare for swift development and implementation of robust cybersecurity measures.
Template benefits include:
- Enhanced credibility through demonstrable expertise in risk management methodologies
- Increased user engagement metrics through practical, implementable security frameworks
- Expanded visibility via natural link acquisition from resource-seeking professionals
- Streamlined compliance assistance that positions the organization as an authoritative reference point
Building Authority Through Technical Security Expertise

Organizations seeking to establish authority in the cybersecurity landscape must deploy thorough technical audits that examine system vulnerabilities, compliance gaps, and operational readiness. According to industry statistics, these practices remain critical yet underutilized among 90% of businesses. This importance is underscored by the fact that only 22% of organizations find their cybersecurity efforts completely satisfactory. Implementing robust security headers can further enhance both security posture and search visibility.
Security certifications, including industry standards such as ISO 27001, SOC 2, and NIST frameworks, serve as third-party validations that markedly enhance credibility and inspire confidence among potential clients facing the escalating $10.5 trillion cybercrime threat landscape. Through the strategic publication of audit methodologies, certification achievements, and technical documentation within dedicated resource pages, companies can position themselves as authoritative voices amid the four-million-professional talent shortage. This approach subsequently attracts both qualified traffic and valuable backlinks from industry publications.
Technical Audits Matter
Thorough technical security audits form the cornerstone of an organization’s cybersecurity posture, enabling proactive vulnerability identification and strategic risk mitigation before malicious actors can exploit system weaknesses.
Technical audit benefits extend beyond mere vulnerability assessment, as they fundamentally transform organizational security readiness, particularly in industries where data breaches carry substantial financial implications. A systematic examination of the organization’s security controls is essential for maintaining business continuity and ensuring operational resilience.
- Extensive network vulnerability assessments identify critical system weaknesses that could otherwise remain undetected until exploitation occurs.
- Regular auditing processes considerably reduce human error, which research indicates accounts for 88% of data breaches.
- Properly executed technical audits guarantee regulatory compliance across industry standards.
- Implementation of audit-recommended security protocols enhances stakeholder trust through demonstrated commitment to data protection.
Credibility Through Certificates
Establishing credible authority in the cybersecurity landscape requires demonstrable expertise through recognized certifications, which serve as fundamental validation mechanisms for professionals seeking to differentiate themselves in an increasingly competitive technical security environment.
Industry-recognized credentials, including CompTIA Security+, CISSP, and CEH, greatly enhance professional standing by providing verification of technical competencies that align with established industry standards.
Additionally, as the cybersecurity sector experiences projected growth of 32% through 2032, certificate value increases proportionally, offering practitioners substantial market differentiation while simultaneously addressing the current deficit of 457,398 unfilled positions within the American job market. Employers frequently list certifications as required qualifications in their job listings, making them essential for career advancement.
Outreach Strategies for Cybersecurity Resource Page Inclusion

When developing thorough outreach strategies for cybersecurity resource page inclusion, professionals must strategically implement multi-faceted approaches that address the unique challenges of this highly specialized field.
Effective partnership development requires meticulous analysis of potential collaborators’ needs, while message personalization demands crafting communications that resonate with security-conscious stakeholders. Establishing business alignment ensures that outreach efforts effectively meet organizational objectives.
Successful cybersecurity outreach necessitates:
- Targeted messaging tailored to high-value cybersecurity accounts, incorporating technical specificity and demonstrating domain expertise.
- Strategic collaboration through established channels, leveraging existing departmental partnerships.
- Active participation in industry-specific events to cultivate professional relationships.
- Development of customized content addressing emerging threats, thereby positioning resources as authoritative reference points.
Creating a central webpage for all awareness materials ensures accessibility and helps consolidate cybersecurity resources that other departments can easily reference and link to.
Measuring the SEO Impact of Your Resource Page Strategy
Once outreach campaigns have secured placements on relevant cybersecurity resource pages, organizations must implement thorough measurement frameworks to quantify returns and evaluate strategic effectiveness.
Utilizing advanced SEO Measurement Tools, including Google Analytics and backlink analyzers, enables precise tracking of referral traffic, conversion rates, and domain authority improvements that result directly from resource page inclusion. Additionally, measuring organic traffic value helps in understanding the effectiveness of SEO investments tied to these resource pages.
Furthermore, monitoring Audience Engagement metrics, such as time on page and bounce rates, provides critical insights into content relevance and user satisfaction, which, when correlated with keyword ranking improvements and backlink quality assessments, creates a detailed performance dashboard that facilitates data-driven refinements to ongoing resource page strategies. Regular security audits should be conducted alongside SEO performance monitoring to ensure resource pages maintain secure coding practices that protect against potential vulnerabilities.
Avoiding Common Resource Page Pitfalls in the Security Niche
Despite the significant potential of resource pages to enhance cybersecurity SEO performance, organizations frequently encounter substantial technical and strategic obstacles that can undermine their effectiveness, diminish search visibility, and ultimately compromise authority within this highly specialized niche.
Resource pages offer immense SEO potential, yet technical pitfalls often sabotage visibility and authority in the cybersecurity niche.
When developing resource page best practices, security professionals must vigilantly avoid these common pitfalls:
- Excessive keyword density that triggers algorithmic penalties, particularly when technical terms like “threat intelligence” become unnaturally repetitive.
- Outdated information that diminishes credibility in this rapidly evolving field. Search engines prioritize secure websites in their ranking algorithms, making outdated security information particularly damaging to both user trust and SEO performance. Regular updates to SSL/TLS infrastructure help maintain credibility and compliance.
- Inadequate technical optimization, including missing schema markup for cybersecurity services.
- Generic content lacking expert-driven keyword strategy insights that specifically address the decision-making terminology used by security professionals.
Future-Proofing Your Cybersecurity Resource Pages for Long-Term SEO Value

As search algorithms continuously evolve alongside emerging cybersecurity threats, organizations must strategically architect their resource pages with adaptable foundations that will maintain relevance, authority, and visibility throughout algorithm iterations and industry paradigm shifts. Implementing thorough mobile optimization guarantees accessibility across devices, while cultivating content variety through infographics, video tutorials, and interactive tools creates multiple engagement pathways for diverse user preferences. Additionally, trust indicators such as security badges can significantly enhance user confidence in the resources provided.
Forward-thinking cybersecurity firms, recognizing that search behaviors increasingly shift toward mobile interfaces, must prioritize responsive design elements that seamlessly adjust to various screen dimensions, thereby preserving user experience quality regardless of access method. Establishing topical authority through comprehensive resource pages enhances domain credibility and improves search engine ranking positions in the competitive cybersecurity landscape.
Build Resource Pages into Your Cybersecurity SEO Strategy!
Resource pages represent an indispensable asset within cybersecurity SEO strategy, offering organizations a systematic methodology to establish authority, generate quality backlinks, and enhance organic visibility within this competitive niche. By developing extensive, technically accurate content assets that address critical security challenges, while implementing strategic outreach initiatives to secure placements on authoritative industry platforms, cybersecurity entities can effectively leverage resource pages as sustainable, long-term drivers of organic search performance.
Frequently Asked Questions
How Long Does It Take for Resource Pages to Generate Quality Backlinks?
Resource pages typically generate quality backlinks within 1-3 months when supported by strategic link building efforts. Success depends on exceptional quality content and consistent outreach to relevant industry authorities.
Should Resource Pages Be Gated Behind Email Sign-Ups?
Gating resource pages behind email sign-ups creates a trade-off between lead capture and visibility. While gated content improves email conversion, it typically reduces SEO performance, sharing potential, and audience reach. Progressive disclosure often yields superior outcomes.
How Often Should Cybersecurity Resource Pages Be Updated?
Cybersecurity resource pages require monthly resource page maintenance to maintain content relevance. Critical security developments may necessitate immediate updates, while thorough quarterly refreshes guarantee cutting-edge information and ideal technical accuracy.
Can Resource Pages Negatively Impact Site Loading Speed?
Resource pages can slow site speed if poorly implemented. Loading speed analysis reveals that strategic resource page optimization through compression, lazy loading, and minification techniques preserves performance while delivering valuable content.
What Percentage of SEO Value Comes from Resource Page Backlinks?
While specific percentage attribution isn’t documented, resource page effectiveness within backlink strategy contributes notably to SEO value, particularly when these pages contain informative content that naturally attracts authoritative industry links.


