Why Spend the Time To Identify Top Cybersecurity Software Buyers Keywords?
The identification of high-value cybersecurity software buyers keywords requires systematic analysis of search patterns across various stakeholder levels within organizations. Security professionals, when initiating procurement processes, frequently employ terminology that reflects compliance requirements, threat mitigation capabilities, and integration parameters rather than generic security terms. Additionally, as cybersecurity threats evolve with increasing sophistication, buyer search behavior adapts accordingly, shifting from basic protection queries toward advanced concepts such as zero-trust architecture, endpoint detection and response (EDR), and cloud security posture management. These linguistic markers reveal underlying priorities and concerns that drive purchasing decisions.
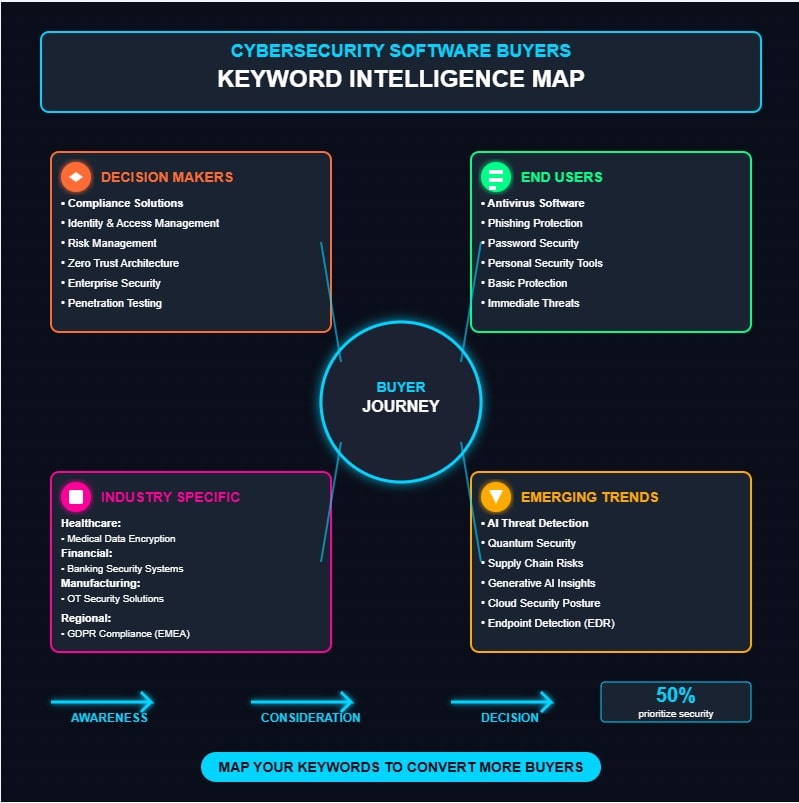
Key Takeaways
- Decision-makers frequently search for “compliance solutions,” “identity and access management,” and “risk management” keywords.
- Technical security terms like “Zero Trust implementations” and “AI-driven threat detection” show rising search interest.
- Industry-specific keywords include “healthcare data encryption,” “financial compliance solutions,” and “OT security for manufacturing.”
- Keywords vary by region with GDPR compliance dominant in EMEA and infrastructure security prevalent in APAC.
- End-user searches focus on “antivirus software,” “phishing protection,” and other immediate threat prevention terms.
Understanding the Cybersecurity Software Purchase Journey

Five critical factors influence the modern cybersecurity software acquisition process, establishing a complex decision-making framework for organizations traversing an increasingly hostile digital landscape.
Within this journey, buyer behavior consistently demonstrates prioritization of security features over cost considerations, with 50% of US businesses citing security as their primary decision factor.
Additionally, as organizations evaluate potential solutions, they increasingly demand thorough security capabilities, including data encryption, automated backups, and real-time threat notifications. Nearly half of businesses have ceased using software due to security issues, underscoring the critical importance of robust protection measures.
In addition, national cybersecurity strategies, competitive market pressures, and industry reports notably shape the evaluation criteria that businesses employ when selecting vendors capable of delivering robust, secure-by-design software solutions.
High-Volume Cybersecurity Software Buyers Keywords in Enterprise Security Solutions
The digital bulwark surrounding modern enterprises increasingly depends on precise keyword utilization within security architecture planning, with organizations leveraging search analytics to identify prevalent threats and corresponding protective measures.
Analysis of enterprise search patterns reveals substantial interest in advanced endpoint protection strategies, particularly solutions addressing remote work vulnerabilities and zero-day exploits.
Furthermore, cloud security trends dominate organizational queries, with significant volume around Zero Trust implementations, AI-driven threat detection systems, and XDR platforms that provide extensive visibility.
Additionally, search data indicates growing enterprise concern regarding insider threats, behavioral analytics, and compliance-focused solutions that adapt to evolving regulatory frameworks—reflecting the cybersecurity landscape’s continuous transformation toward proactive, intelligence-driven defense mechanisms. Organizations are increasingly searching for effective strategies to counter the rising threat of deepfake attacks used in sophisticated social engineering campaigns.
Decision-Maker Keywords vs. End-User Search Patterns
Despite operating within the same cybersecurity ecosystem, executive decision-makers and end-users demonstrate markedly divergent search patterns that reflect their distinct roles, responsibilities, and cybersecurity knowledge bases, creating significant implications for software vendors’ keyword optimization strategies. Effective keyword targeting requires understanding audience segmentation by professional roles and specific security needs.
| Category | Decision-Maker Trends | End-User Concerns |
|---|---|---|
| Primary Focus | Compliance, IAM, Risk Management | Antiviruses, Phishing Protection, Passwords |
| Technical Depth | Enterprise-level solutions, Penetration testing | Personal security tools, Basic protection |
| Budget Consideration | Scalability, Long-term ROI | Affordability, Ease of implementation |
| Regulatory Interest | Security certifications (46% priority), Compliance | Simple protection, Immediate threats |
| Terminology Used | Advanced technical terms, Industry standards | Simplified security concepts, Threat names |
Emerging Trends in Cybersecurity Software Search Terms

Beyond the stark contrasts between decision-maker and end-user search behaviors, cybersecurity keyword landscapes continually evolve as emerging threats and technological innovations reshape the security paradigm.
Within this rapidly shifting environment, search queries increasingly focus on AI Threat Detection capabilities, which leverage machine learning to identify anomalous patterns that conventional systems might overlook. The escalating threat landscape has driven organizations to prioritize Zero Trust Architectures that require authentication for every access request, regardless of source or location.
Simultaneously, Quantum Security Challenges are driving significant interest in post-quantum cryptography solutions, while Supply Chain Risks have prompted searches for thorough vendor assessment tools.
Additionally, Generative AI Insights have emerged as critical search terms, reflecting the industry’s pivot toward using artificial intelligence for analyzing unstructured security data with unprecedented efficiency.
Industry-Specific Security Software Keywords
Healthcare organizations, which manage vast repositories of sensitive patient data and must comply with HIPAA regulations, frequently search for “healthcare threat protection,” “medical data encryption,” and “patient information security solutions” when seeking specialized cybersecurity software.
Financial institutions, operating under strict regulatory frameworks including SOX, GLBA, and PCI DSS, demonstrate significant interest in “financial compliance solutions,” “banking security systems,” and “fraud detection software” to safeguard monetary transactions and customer financial records. Security professionals in this sector also frequently search for “SIEM solutions” to monitor for threats, with this technology commanding a high CPC of $3.13 due to its critical importance in threat detection.
The manufacturing sector, increasingly vulnerable due to IoT implementation and industrial control systems, commonly seeks “OT security solutions,” “industrial network protection,” and “manufacturing compliance software” to address their unique cybersecurity challenges within operational technology environments.
Healthcare Threat Protection
The five most critical keywords for healthcare cybersecurity software reflect the industry’s unique vulnerability landscape, which continues to evolve as digital transformation accelerates throughout medical institutions globally.
With healthcare data privacy remaining the paramount concern for software purchasing decisions, organizations increasingly allocate budget toward ransomware threat mitigation solutions.
The unprecedented 18.55% market growth rate directly correlates to escalating threats targeting patient information ecosystems.
Consequently, keywords related to AI-driven defense mechanisms, zero-trust architectures, and FDA-compliant security frameworks dominate search patterns as healthcare institutions prepare against sophisticated attacks that exploit cloud vulnerabilities, session-based weaknesses, and historical data repositories.
Nearly 45% of healthcare buyers cite data security as the biggest barrier to adopting new software solutions for their organizations.
Financial Compliance Solutions
| Financial Compliance Solutions | Primary Regulatory Focus |
|---|---|
| Centraleyes | PCI DSS, GDPR |
| VComply | Cloud-based GRC Management |
| SIEM Solutions | Security Monitoring |
| IAM Systems | Identity Management |
| Cyber AI Platforms | Threat Detection |
Financial regulatory compliance necessitates specialized compliance management software that supports multiple frameworks simultaneously, thereby eliminating redundant processes while maintaining operational resilience. Additionally, effective solutions must address the sector’s unique challenges, including data breach prevention, anti-fraud measures, and ransomware mitigation, while simultaneously satisfying stringent requirements from FINRA, DORA, and SOC 2 certifications. Regular risk assessments are essential for identifying compliance deficiencies and ensuring adherence to evolving cybersecurity regulations in the financial industry.
Mapping Keywords to Buyer Personas in Cybersecurity
Effective keyword mapping represents a critical juncture between technical SEO implementation and strategic marketing alignment, particularly when cybersecurity vendors seek to connect with diverse decision-makers across organizational hierarchies.
Through extensive buyer persona development, organizations can systematically align keywords with demographic insights and pain point analysis, thereby creating a framework for targeted content development that resonates with specific decision factors. Additionally, 68% of online experiences begin with a search engine, underscoring the importance of optimizing for relevant keywords in the cybersecurity space.
Subsequently, this strategic keyword alignment necessitates thorough risk assessment and evaluation of content preferences, which, when properly executed, enables cybersecurity vendors to develop engagement strategies that generate higher conversion rates across diverse stakeholder groups with varying levels of technical expertise and purchasing authority.
Marketers can segment their email lists to deliver more personalized messages that address the unique challenges faced by different cyber security personas, improving overall campaign effectiveness.
Competitive Keyword Analysis for Security Software Vendors
Building upon the foundation of persona-driven keyword strategies, competitive keyword analysis emerges as a cornerstone practice for security software vendors seeking market differentiation in an increasingly crowded cybersecurity landscape.
Through dedicated competitor analysis tools such as Ahrefs, SEMrush, and Similarweb, vendors can systematically identify keyword gaps and SERP feature opportunities that competitors may have overlooked, while simultaneously evaluating keyword metrics including search volume, competition levels, and seasonal fluctuations. Additionally, 63% of all shopping begins online, even for cybersecurity solutions, illustrating the importance of a robust online presence.
Additionally, by conducting thorough keyword gap analysis, security software organizations can discover high-value, low-competition terms in specialized areas like identity and access management or penetration testing, thereby creating targeted content strategies that elevate visibility while reducing redundant bidding wars in saturated keyword marketplaces. These strategies should incorporate niche service leads such as “penetration testing near me” to capture location-specific prospects actively seeking cybersecurity solutions.
The Role of Certifications in Security Software Selection

Five critical cybersecurity certifications have emerged as powerful indicators of software reliability and expertise in today’s complex threat landscape, where organizations increasingly demand evidence-backed assurance before committing to security solutions.
The certification impact on purchasing decisions manifests through enhanced software credibility, demonstrated vendor competence, and alignment with regulatory frameworks that organizations must navigate in their security governance strategies. Projected 32% growth rate in cybersecurity jobs from 2022 to 2032 further underscores the importance of certified professionals in evaluating and implementing security software. As organizations seek to improve their local search queries, certified professionals play a vital role in ensuring that security software meets industry standards.
- CISSP certification signals deep security expertise across multiple domains, influencing buyers seeking extensive protection solutions.
- CEH credentials validate practical penetration testing capabilities, appealing to those prioritizing offensive security features.
- CISA/CISM certifications demonstrate governance-focused approaches, attracting enterprises concerned with regulatory compliance.
From Search Intent to Purchase: Tracking the Keyword Funnel
The journey from search queries to conversion in cybersecurity software marketing requires granular analysis of how potential clients move through awareness, consideration, and decision stages, each characterized by distinct keyword patterns.
Throughout this funnel, understanding search intent enables companies to strategically position content that addresses specific pain points, such as “data breach prevention solutions” for awareness and “endpoint security software comparison” for consideration phases. Notably, over 7 billion searches are conducted on Google daily, highlighting the importance of keyword optimization in capturing organic traffic. Effective analysis should include monitoring keyword performance continuously, allowing for strategic adjustments that enhance visibility and lead generation efforts.
Understanding Search Patterns
How potential customers navigate the cybersecurity software marketplace reveals critical insights that vendors must leverage to optimize their digital marketing strategies, particularly as the journey from initial awareness to final purchase follows distinct, trackable patterns of keyword usage across multiple stages.
Understanding searcher motivations requires analyzing the evolutionary nature of queries, which transform from general threat concerns during awareness phases into specific product evaluations during decision-making processes, while maintaining keyword relevancy throughout the entire funnel. Organizations are increasingly concerned about data breaches, which now cost approximately $4.88 million on average according to IBM’s 2024 report.
- Awareness-stage searches typically focus on threat education and industry statistics
- Consideration-stage queries emphasize vendor comparisons and security certification requirements
- Decision-stage keywords concentrate on implementation specifics, pricing structures, and integration capabilities
Converting Keywords Into Sales
Transforming keyword research into measurable sales results requires cybersecurity vendors to systematically analyze search intent patterns, identifying precisely where prospects position themselves within the purchase funnel before strategically aligning content and marketing initiatives to these behavioral signals.
Successful keyword strategies follow prospects through their customer journey, from awareness-stage searches like “what is cyber security” (educational content), through consideration-stage queries such as “cyber security training” (professional development), to decision-stage terms including “cybersecurity software” (purchasing readiness). Effective campaigns should address specific threat vectors like phishing attacks, as phishing remains the most recognized cybersecurity threat among potential buyers.
Regional Variations in Cybersecurity Software Search Terms
Across diverse global regions, cybersecurity software search trends reveal distinctive patterns that reflect unique regulatory environments, technological infrastructures, and threat landscapes facing organizations.
Regional keyword analysis demonstrates that EMEA prioritizes GDPR compliance and cloud security, while APAC focuses mainly on 5G security and supply chain risks, illustrating significant cybersecurity language differences across markets.
- EMEA region: Regulatory-focused terminology centered on compliance frameworks, with ransomware protection emerging as a critical concern.
- Americas region: Operational security emphasis, particularly regarding insider threats and tactical AI implementation.
- APAC region: Infrastructure-centric keywords related to 5G security and nation-state threats.
The search behavior in all regions increasingly reflects concerns about machine identities as organizations struggle with the expanded attack surface created by uncontrolled credentials from AI and cloud services.
Identify the Top Cybersecurity Software Buyers Keywords to Help Focus your Website!
Identifying top keywords that cybersecurity software buyers search for requires a multifaceted approach that differentiates between decision-maker and end-user search patterns, while simultaneously accounting for industry-specific terminology, regional variations, and evolving threat landscapes. Organizations that strategically incorporate these nuanced keyword insights into their marketing frameworks, particularly emphasizing compliance, IAM, and risk management for executives versus simpler security terms for end-users, will ultimately capture more qualified leads throughout the complex cybersecurity purchase journey.
Frequently Asked Questions
How Do ROI Metrics Influence Cybersecurity Software Purchase Decisions?
ROI metrics drive cybersecurity software purchase decisions by providing quantitative validation through ROI analysis, enabling organizations to objectively compare solutions during software evaluation and justify investments to executive stakeholders.
What Impact Do Recent Breaches Have on Security Keyword Trends?
Recent breaches accelerate keyword evolution toward protection-focused terms. Breach repercussions drive surges in searches for vulnerability management, zero-trust architecture, and advanced threat detection solutions among security-conscious organizations.
How Do Free Versus Premium Security Software Search Patterns Differ?
Free software searches favor basic protection and immediate solutions, while premium software searches emphasize advanced features, enterprise integration, and brand reputation. User preferences reflect organizational needs versus consumer behavior prioritizing cost-effectiveness.
Which Pricing Models Are Most Searched for Cybersecurity Solutions?
Subscription models dominate search patterns for cybersecurity solutions, followed by usage-based pricing. Enterprises increasingly explore flexible licensing options that scale with organizational needs while minimizing upfront capital expenditure commitments.
What Deployment Options Are Most Frequently Searched in Cybersecurity Software?
Buyers frequently search for cloud deployment options, offering scalability and accessibility, alongside on-premises solutions providing greater control and compliance capabilities within cybersecurity software ecosystems. Hybrid models increasingly attract security-conscious innovators.


