The evolution of incident response solutions demands strategic landing page design, with key features serving as critical conversion points for security-conscious stakeholders. Well-crafted incident response solution landing pages, functioning as digital frontlines for cybersecurity offerings, must balance technical specificity with accessibility to effectively communicate value propositions. Organizations implementing these solutions, particularly those facing increasing regulatory scrutiny and sophisticated threat vectors, require immediate visual confirmation that a product addresses their specific vulnerability landscape. What essential components separate high-performing incident response solution landing pages from ineffective ones?
Key Takeaways
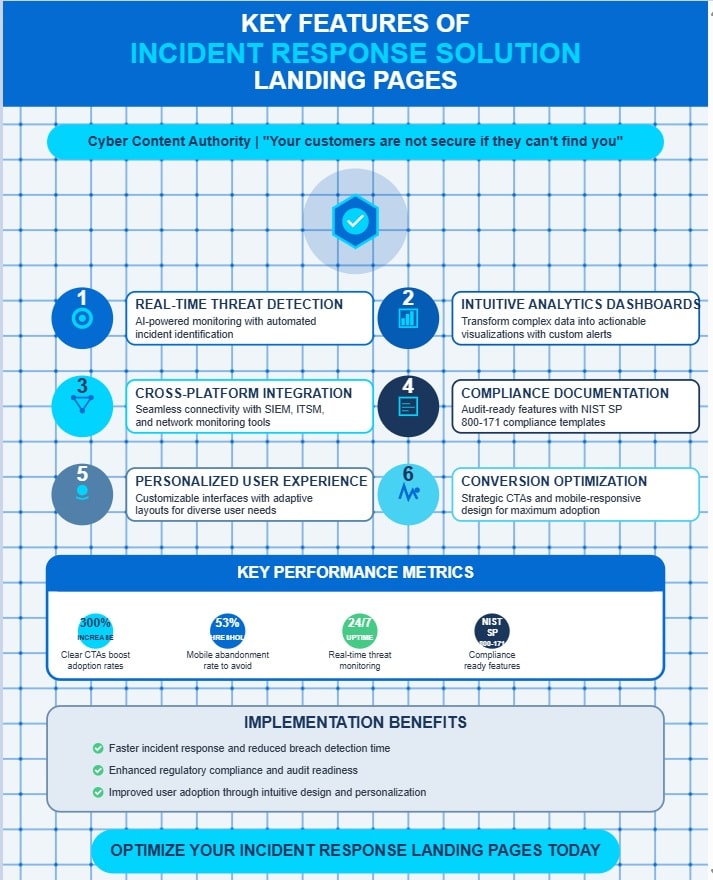
- Real-time threat detection systems integrate AI algorithms to identify potential security incidents quickly while minimizing false positives.
- Intuitive analytics dashboards transform complex security data into actionable visualizations with customizable alerting thresholds.
- Cross-platform data integration creates a unified security view by connecting SIEM, IT service management, and network monitoring tools.
- Compliance-ready features automate documentation with pre-formatted templates that align with regulations like NIST SP 800-171.
- Conversion-optimized designs use simplified language, prominent CTAs, and mobile responsiveness to increase solution adoption rates.
Real-Time Threat Detection and Monitoring Capabilities

Every sophisticated security posture requires robust real-time threat detection and monitoring capabilities that serve as the frontline defense against evolving cyber threats.
Within today’s rapidly shifting threat landscapes, continuous monitoring systems identify potential security incidents before significant damage occurs, thereby minimizing operational disruption and reducing costs associated with breaches.
Advanced security technologies, incorporating AI and machine learning algorithms, enable organizations to distinguish genuine threats from false positives while providing round-the-clock defense through automated processes. These solutions help organizations maintain compliance with regulations such as GDPR and HIPAA, offering significant risk mitigation through detailed reporting capabilities for audits.
AI-driven security technology separates real threats from noise, delivering 24/7 protection through intelligent automation
Consequently, these capabilities facilitate not only rapid incident response but also strengthen an organization’s ability to adapt proactively to emerging threat vectors through enhanced threat intelligence and extensive data analysis.
Intuitive Analytics Dashboards for Incident Visualization
Modern incident response solutions feature extensive dashboards that transform complex security data into actionable visualizations, enabling teams to identify threats, patterns, and anomalies through real-time threat visualization capabilities.
Through customizable alerting thresholds, security teams can fine-tune detection parameters according to their organization’s unique risk profile, preventing both alert fatigue from excessive notifications and dangerous blind spots from insufficient monitoring.
Cross-platform data integration, a cornerstone of effective analytics dashboards, allows security professionals to correlate events across disparate systems, networks, and applications, creating a unified view of the security landscape that highlights potential attack vectors which might otherwise remain obscured when examining isolated data sources. Teams can efficiently analyze incident data by selecting appropriate visualization types from timeseries line graphs to categorical breakdowns, ensuring optimal representation of critical metrics.
Real-Time Threat Visualization
Consistently, real-time threat visualization serves as the cornerstone. These intuitive analytics dashboards enable security teams to continuously monitor system operations and detect suspicious activities, providing proactive threat detection that significantly reduces response time and minimizes potential damage from security incidents.
Customizable Alerting Thresholds
While effective incident response depends on timely detection, customizable alerting thresholds provide the critical foundation for security teams to distinguish between normal network behavior and genuine threats, thereby reducing alert fatigue and accelerating response times.
Organizations implementing sophisticated alerting strategies can greatly improve SLA compliance and optimize resource allocation, as thresholds can be configured based on incident type, priority, and historical patterns.
These systems, which integrate seamlessly with existing security infrastructure, enable the creation of customizable notifications that trigger only when predefined conditions are met, minimizing false positives while ensuring critical incidents receive immediate attention.
Modern solutions implement mobile accessibility features that allow security personnel to adjust thresholds and respond to alerts from anywhere, ensuring continuous monitoring capabilities regardless of location.
Through data-driven threshold configuration, security teams transform reactive monitoring into proactive threat management.
Cross-Platform Data Integration
Sophisticated incident response solutions leverage the power of cross-platform data integration, creating an extensive operational framework that synthesizes critical information from disparate sources into a cohesive, actionable intelligence stream.
Through advanced data synchronization mechanisms, these solutions amalgamate inputs from SIEM systems, IT service management tools, and network monitoring platforms, enabling thorough visibility across the enterprise security landscape.
Moreover, platform interoperability, facilitated through robust API connectivity, guarantees that real-time updates flow seamlessly between systems, thereby maintaining dashboard accuracy regardless of originating data sources.
This unified approach, which scales effectively to accommodate growing data volumes, fundamentally transforms fragmented security information into a strategic asset for incident response teams.
An effective dashboard consolidates key metrics like open incidents and SLA compliance rates, providing real-time snapshots of incident management performance.
Personalize User Experience and Interface Design for Better Incident Response Solution Landing Pages
To create truly effective incident response landing pages, organizations must implement personalized user experiences and intuitive interface designs that accommodate diverse user needs, technical capabilities, and situational contexts.
Through systematic user persona development and continuous user feedback integration, landing pages can evolve to reflect the specific requirements of security professionals, executives, and technical teams.
The implementation of customizable interfaces, featuring modular components and adaptive layouts, guarantees that critical incident response information remains accessible across all devices.
Meanwhile, task-oriented navigation structures guide users efficiently through decision pathways during high-stress scenarios. Ensuring multiple update subscription options allows stakeholders to stay informed as the emergency situation evolves.
Seamless Integration With Existing Security Infrastructure

Seamless integration with existing security infrastructure represents the foundation upon which effective incident response solutions must be constructed. This enables organizations to extend their security capabilities without disrupting established protocols or implementation architectures.
When selecting incident response platforms, organizations must consider how these systems overcome integration challenges while maintaining robust security protocols across the environment. Platforms like IBM Security QRadar SOAR provide detailed workflows that integrate smoothly with existing security stacks.
Key integration capabilities include:
- API connectivity with firewalls and IDS systems
- SIEM compatibility for extensive data analysis
- Automated incident detection with machine learning integration
- Real-time monitoring and prioritization mechanisms
Through strategic integration, organizations achieve enhanced security posture, rapid response times, and efficient resource utilization across the enterprise. This creates a thorough defense framework that leverages existing investments while addressing evolving threat landscapes.
Compliance Documentation and Audit-Ready Features
Thorough compliance documentation and audit-ready features constitute three essential pillars of effective incident response platforms, providing organizations with the necessary infrastructure to satisfy regulatory requirements while maintaining operational readiness for both planned and surprise audits.
Modern platforms incorporate automated reporting systems with pre-formatted compliance templates that align with NIST SP 800-171 and other standards, considerably reducing preparation time for audit procedures.
Additionally, centralized documentation databases, equipped with robust access controls and version tracking, guarantee data integrity throughout incident lifecycle management. These systems can effectively standardize incident response across organizations while ensuring all documentation meets regulatory requirements.
Extensive compliance training modules, integrated directly within these solutions, enable teams to maintain regulatory knowledge while implementing consistent documentation practices that transform incident insights into continuous improvement opportunities.
Conversion Optimization for Security Solution Adoption
Converting visitors into adopters stands as the ultimate goal of any incident response solution landing page, requiring strategic optimization techniques that maximize engagement while reducing friction throughout the visitor’s decision journey.
Through data-driven design modifications, organizations can establish customer trust while markedly improving performance metrics, as evidenced by studies showing even small conversion improvements yielding substantial results. Incident response solution landing pages with simplified language written at a 5th-7th grade level typically achieve significantly higher conversion rates compared to those using more complex terminology. Additionally, with over 7 billion searches conducted on Google daily, visibility in search results can significantly influence conversion rates.
- Clear, prominently positioned CTAs increase adoption rates by up to 300%
- Mobile optimization addresses the critical 53% abandonment threshold
- Personalized content demonstrating industry-specific protection delivers 202% higher conversions
- Security trust indicators and compliance certification displays reinforce credibility
When strategically implementing these optimization elements, companies with dedicated incident response solution landing pages for distinct security solutions consistently outperform competitors.
This is particularly true when deployment speed and implementation structure receive equal optimization attention.
Build Effective Incident Response Solution Landing Pages to Improve Your Conversions!
Effective incident response solution landing pages, through their strategic integration of real-time monitoring capabilities, intuitive visualization tools, and compliance documentation features, establish a foundation for robust security posture while simultaneously addressing conversion optimization needs. Organizations that implement these key features, particularly when coupled with personalized user experiences and seamless infrastructure integration, position themselves advantageously within the increasingly complex cybersecurity landscape, ultimately driving adoption through demonstrated technical competence and user-centric design.
Frequently Asked Questions
How Quickly Can Security Teams Implement an Incident Response Solution?
Implementation speed varies from days to weeks depending on team readiness, existing infrastructure, and solution complexity. Organizations with established protocols can deploy faster than those starting from scratch.
What Are the Typical Training Requirements for Staff Using These Platforms?
Staff typically require thorough user training in platform proficiency, including modules on incident analysis, threat assessment, and communication protocols. Organizations should implement ongoing refresher courses to maintain operational readiness for evolving security challenges.
How Do Incident Response Solutions Handle False Positives?
Advanced incident response platforms employ incident classification algorithms and false positive metrics to automate alert triage, continuously refining detection accuracy through machine learning and contextual analysis of security event patterns.
What Is the Average Cost Reduction Compared to Manual Response Methods?
Automated incident response solutions deliver up to 80% cost reduction compared to manual methods, with organizations realizing average savings of $2.2 million by minimizing manual labor and enhancing cost effectiveness across security operations.
Can These Solutions Detect Insider Threats Alongside External Attacks?
Modern incident response solutions excel at both insider threat detection and external attack mitigation through behavioral analytics, real-time monitoring, and machine learning algorithms that identify suspicious patterns across all potential threat vectors.